Category: Articles
-
How to Edit JSON Config Files using Free JSON Editors or Notepad++
JSON (JavaScript Object Notation) is gaining popularity as a format for configuration files. Unlike XML or the still-used INI format, editing JSON in a text editor can be tedious and error-prone. However, there are free JSON editors and plugins for Notepad++ that simplify this task. Initially intended for platform-independent serialization of JavaScript objects, JSON is…
-
How to Add an Azure AD Group to Your Local Administrator Group: A Step-by-Step Guide
This guide will explore adding an Azure Active Directory (Azure AD) group to the local administrator’s group. This will empower Azure AD group members to conduct tasks needing administrator permissions on Windows 10 and Windows 11 computers. The progression to LocalUsersandGroups policy From the release of Windows 10 version 20H2, Microsoft suggests using the LocalUsersandGroups…
-
A Detailed Guide on Analyzing Windows Event Logs Using Security Onion
Security Onion is an open-source platform for threat hunting, security monitoring, and log management. It aggregates free tools such as Kibana, Elastic Fleet, InfluxDB, CyberChef, and Suricata. The solution provides access to these tools via a web console. I’ll demonstrate how it can be used for analyzing Windows logs. Security Onion is designed as a…
-
Step-by-Step Guide to Configure Firefox Proxy Settings Using Group Policy
If you desire to manage the proxy settings of the Mozilla browser in a network in a centralized way, there exists an applicable Group Policy. Different from Google Chrome or Microsoft Edge, Firefox has the potential to not only obtain the proxy configuration from Windows directly but also through GPO. Within numerous organizations, users access…
-
How to Use PowerShell for Managing System and User-Assigned Managed Identities in Azure
Managed identities provide secure authentication for resources accessing other resources in Azure without requiring sensitive information such as secrets, credentials, and certificates to be handled. Microsoft Entra ID manages these identities, enabling applications to obtain tokens for authentication. In this post, I will provide an example that illustrates how to use system and user-assigned managed…
-
How to Manage Docker Using VS Code
You can manage Docker images and containers directly within Visual Studio Code (VS Code) with Microsoft’s Docker extension. This article walks you through adding Docker files to a Workspace, creating a containerized application environment, and explains how to build and run Docker containers directly from the VS Code interface. Prerequisites To follow this guide, you…
-
How to Create a Bootable ISO for a Windows Image (.wim)
Before deploying to clients, it’s critical to update a Windows image with the most recent patches and tailor it according to their requirements. Depending on your deployment technique, the WIM archive may need to be provided on a bootable ISO file. This is something that can be achieved with the tools offered in the Windows…
-
Mastering Complex Network Simulations with GNS3
The free Graphical Network Simulator-3 (GNS3) allows for the planning and practical simulation of networks and their topology. Thanks to Dynamips, it also supports integrating images of Cisco IOS. GNS3 can be integrated with physical hardware, enabling, for instance, the testing of monitoring solutions. In the first step, we install GNS3 on a physical computer,…
-
Step-by-step Guide to Building Your Own ChatGPT App
In my previous post on the OpenAI API, I introduced a simple chatbot that demonstrated how to interact with the API. In this post, I will take it a step further by showing you how to create your own ChatGPT app. You may be wondering why you need your own ChatGPT app when you can…
-
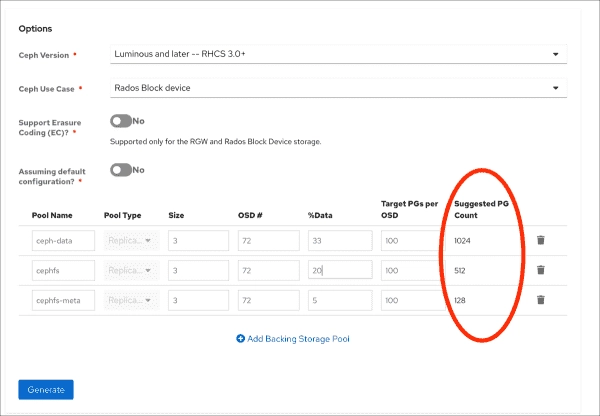
Optimizing Performance with Ceph Tuning
Tuning Ceph performance is crucial to ensure that your Ceph storage cluster operates efficiently and meets the specific requirements of your workload. As Ceph installations, both in software and hardware, are upgraded or as your workload changes, the default tunables that were optimal at one time may now be obsolete or counterproductive. This article assumes…