Category: Security
-
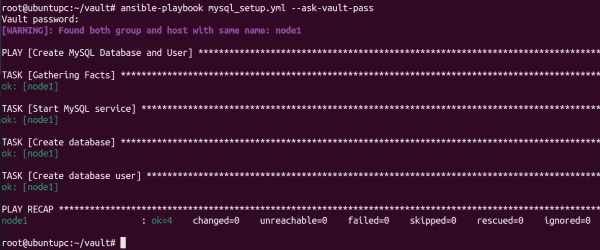
Mastering Encryption and Decryption with Ansible Vault
Ansible Vault allows you to encrypt sensitive data such as passwords, keys, and other secrets rather than storing them as plaintext in your playbooks or roles. In this tutorial, I will explain how to use Ansible Vault to encrypt and decrypt data during playbook runtime. Prerequisites To proceed with this tutorial, you will need the…
-

How to Adjust Privacy Settings in Microsoft Edge: Disabling Tab Grouping, Creator Following, Similar Sites, and Shopping Recommendations
Microsoft regularly uses its platform to push its software and cloud services onto users, often providing little value but bloating the system or siphoning off data. This is applicable to various Edge browser features that are active by default but can be disabled via GPO. Microsoft has long been installing Windows add-ons without user consent.…
-
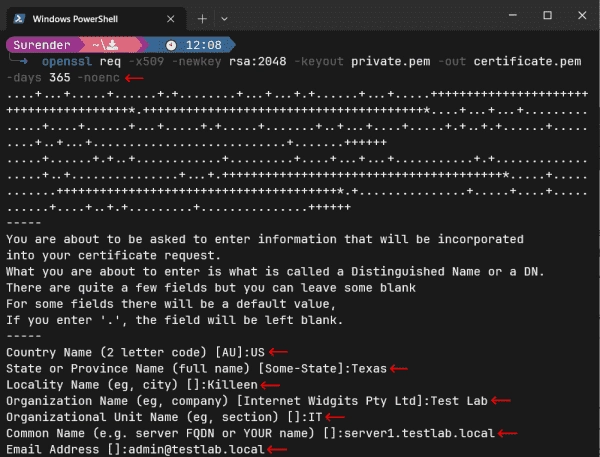
How to Convert Certificate Format Using OpenSSL
OpenSSL is an open-source library and a command-line tool that helps admins and developers perform various cryptographic tasks, such as generating key pairs, certificate signing requests (CSR), verifying certificates, encrypting and decrypting data, identifying certificate information, verifying file integrity and much more. In this post, you will learn how to convert TLS certificates into different…
-
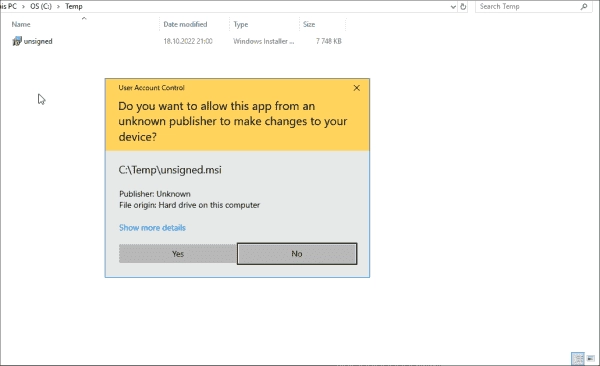
How to Verify Digital File Signatures using SigCheck
SigCheck, part of the SysInternals suite, is a command-line utility offering security features such as verifying the digital file signature and calculating file hashes using multiple hashing algorithms. Distributing digitally signed files to customer computers is a common practice for trusted software publishing companies. The code-signing process uses a certificate from a reliable certification authority…
-
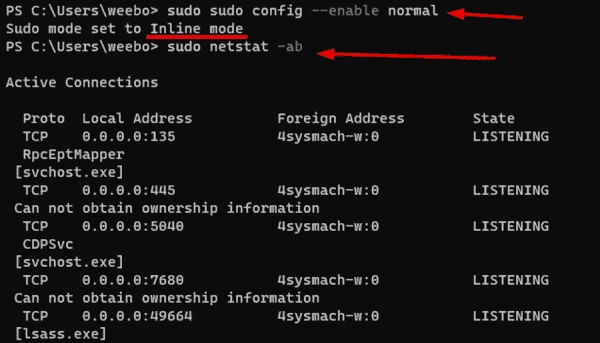
Comparing Sudo for Windows vs. Runas and Sudo for Linux
Sudo for Windows has been available since Build 26052 and is currently only accessible through the Windows Insiders program as part of preview builds for Windows 11. At this time, it appears that sudo will not come to Windows Server 2025. In this article, I explain how to use sudo in Windows 11 and compare…
-
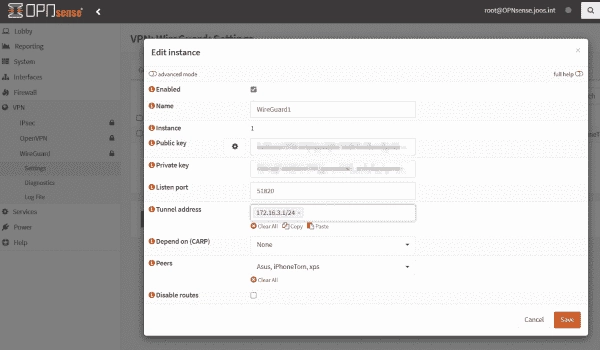
Step-by-Step Guide to Installing WireGuard VPN on OPNsense Firewall
If you are employing an OPNsense firewall, the option to configure WireGuard as a VPN server instead of OpenVPN is a viable option. WireGuard’s clients are available for all major operating systems, proving very fast and lightweight. This can easily be installed as an OPNsense extension and configured via the web console. For implementing a…
-
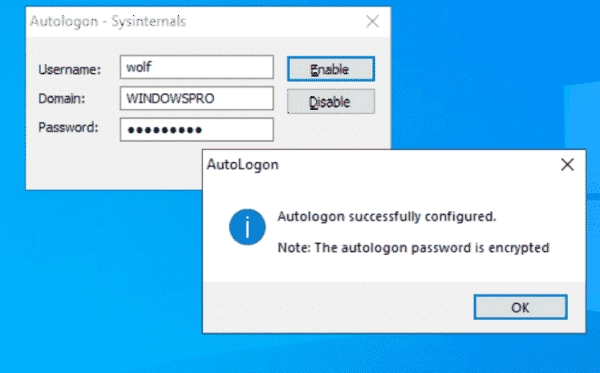
How to Enable Windows Auto-Login Without a Password
Usually, you want to secure your Windows account with a strong password or other authentication methods. However, there may be situations where you want to set up a Windows computer to log in automatically without requiring a password. If only one user operates a PC and the computer is physically protected from unauthorized access, you…
-
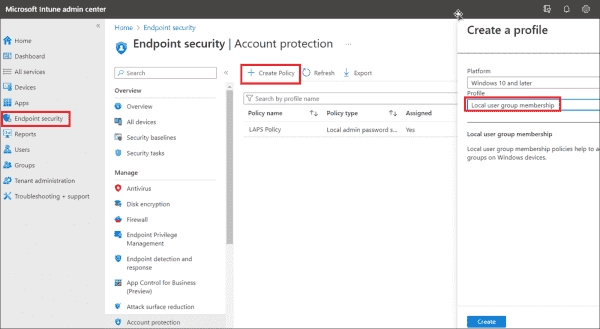
How to Add an Azure AD Group to Your Local Administrator Group: A Step-by-Step Guide
This guide will explore adding an Azure Active Directory (Azure AD) group to the local administrator’s group. This will empower Azure AD group members to conduct tasks needing administrator permissions on Windows 10 and Windows 11 computers. The progression to LocalUsersandGroups policy From the release of Windows 10 version 20H2, Microsoft suggests using the LocalUsersandGroups…
-
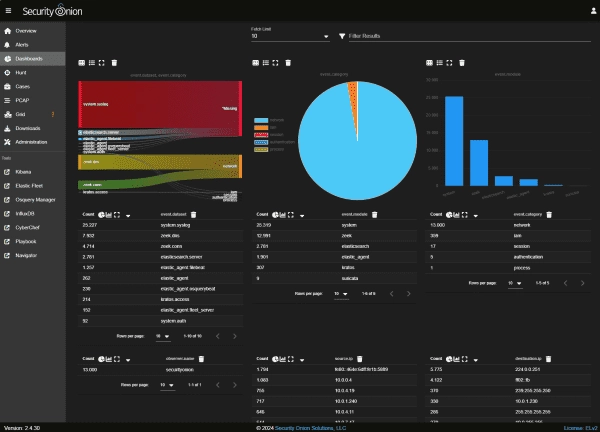
A Detailed Guide on Analyzing Windows Event Logs Using Security Onion
Security Onion is an open-source platform for threat hunting, security monitoring, and log management. It aggregates free tools such as Kibana, Elastic Fleet, InfluxDB, CyberChef, and Suricata. The solution provides access to these tools via a web console. I’ll demonstrate how it can be used for analyzing Windows logs. Security Onion is designed as a…
-
How to Use PowerShell for Managing System and User-Assigned Managed Identities in Azure
Managed identities provide secure authentication for resources accessing other resources in Azure without requiring sensitive information such as secrets, credentials, and certificates to be handled. Microsoft Entra ID manages these identities, enabling applications to obtain tokens for authentication. In this post, I will provide an example that illustrates how to use system and user-assigned managed…