Category: Security
-
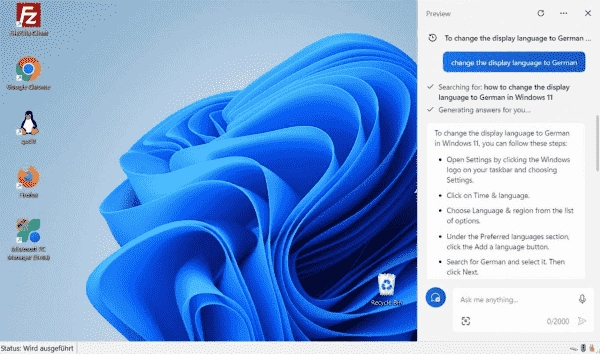
Steps to Disable Copilot and Block ChatGPT on Windows and Edge Using Group Policy and Defender
Microsoft has integrated AI features under the brand Copilot into almost all of its products, including Windows and the Edge browser. For businesses that haven’t developed an AI strategy yet, these consumer versions of Copilot are often undesired. Fortunately, they can be blocked using group policies. In principle, the potential of generative AI for many…
-
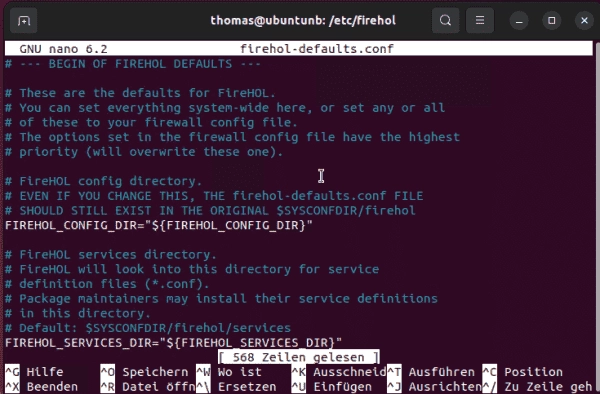
How to Configure iptables Using Firehol: A Comprehensive Guide
Firehol is an open-source tool used to configure Linux firewalls, such as those based on iptables. Advanced users can delve deeper into the rule set with optional parameters. Firehol ensures that the rules are coherent in both directions. By default, Firehol generates rules for both IPv4 and IPv6. This can be changed in the configuration…
-
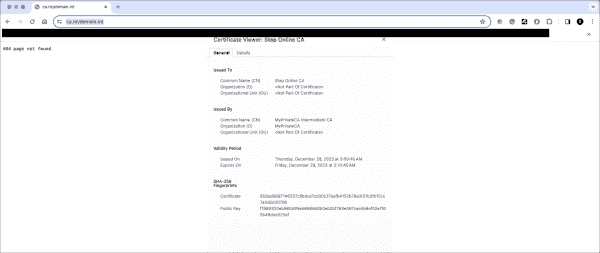
A Guide to Installing and Using the step-ca Certificate Authority Client
The previous article discussed installing an ACME-compatible certificate authority server. This post explains how to install step-cli (ACME client) on a client system to install the new certificate authority (CA), make it trusted, and request a TLS certificate. Install step-cli on a client. Pre-built packages for many operating systems and CPU platforms are on the…
-
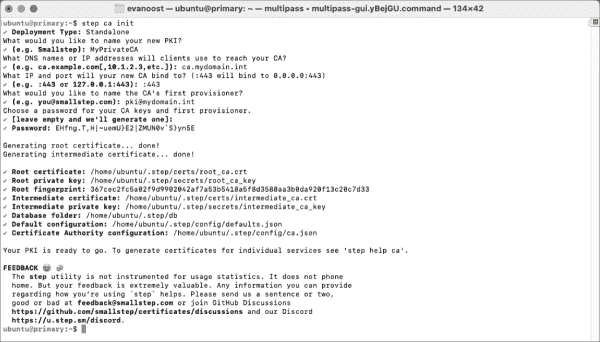
How to Run Your Own Certificate Authority with ACME Support Using Step-ca
Step-ca is a Certificate Authority (CA) management tool for Windows, Linux, and macOS designed to simplify the process of creation, management, and revocation of certificates for use with TLS, mutual TLS (mTLS) authentication, document signing, and other X.509 authentication as well as SSH keys through a variety of provisioners. A provisioner is a method with…
-
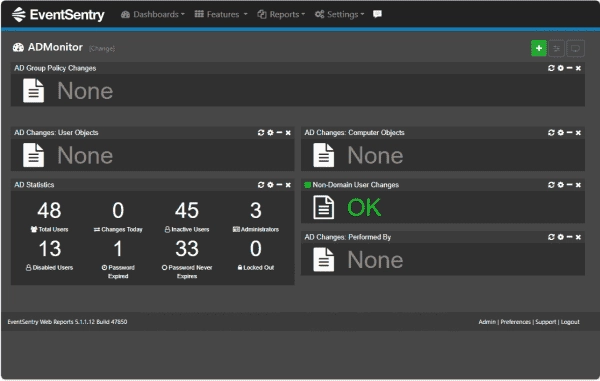
Unveiling EventSentry 5.1: Exploring its New Network Security Monitoring and Compliance Features
Explore the new features in EventSentry 5.1, including anomaly detection, NTFS permissions inventory, and new compliance dashboards. Many log collection and SIEM solutions are available in the market today. A notable solution in this space is EventSentry. EventSentry 5.1 is a recent release that brings numerous enhancements to the platform. Brief overview of EventSentry EventSentry,…
-
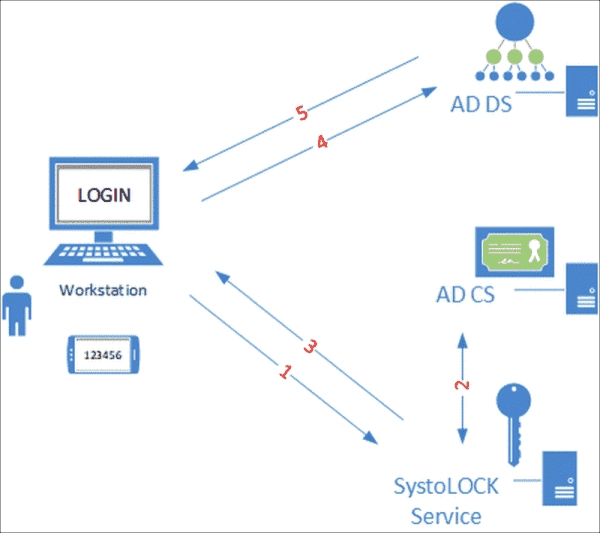
Reviewing SystoLOCK: Multi-Factor Authentication for Active Directory Without Passwords
SystoLOCK presents a sturdy route to boost security using multi-factor authentication (MFA) without requiring passwords in an Active Directory ecosystem. Unlike various other methods, SystoLOCK doesn’t require cloud services. This solution brings about ease similar to smartcard-based authentication, nullifying the requirement for intricate password management. Furthermore, SystoLOCK provides the functionality for users to securely log…
-
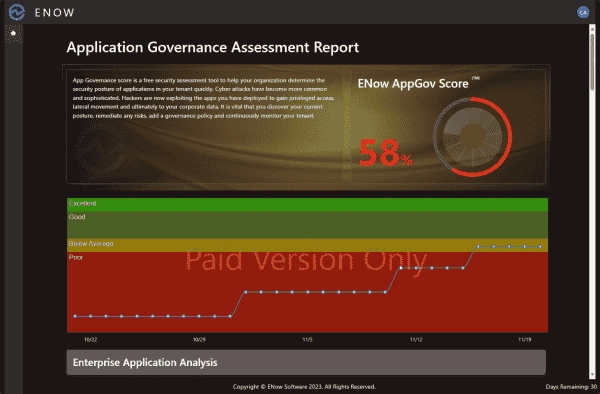
Get Your Free Microsoft Entra ID App Security Assessment with ENow AppGov Score Today!
Many organizations are behind the curve in understanding their SaaS applications and governance. Indeed, SaaS applications and SaaS app governance can pose a serious challenge for many IT admins, particularly in terms of visibility and control. ENow has launched a free assessment tool named AppGov Score that calculates the governance state of Microsoft Entra ID…
-
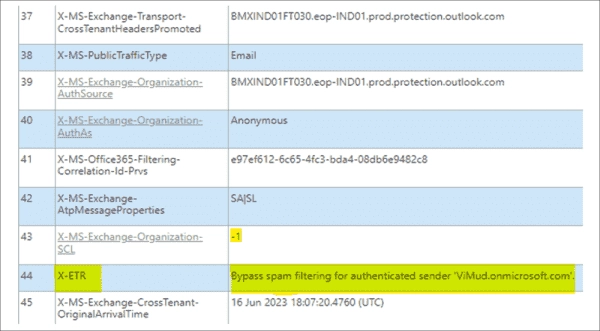
Step-by-Step Guide: How to Whitelist a Domain in Microsoft 365
Defender for Office 365 and Exchange Online Protection monitor all emails coming to your domain, blocking any harmful or spam messages. However, it can sometimes block emails from legitimate sources due to various reasons. As an administrator, you might want to whitelist certain senders or domains. This post will guide you on how to whitelist…
-
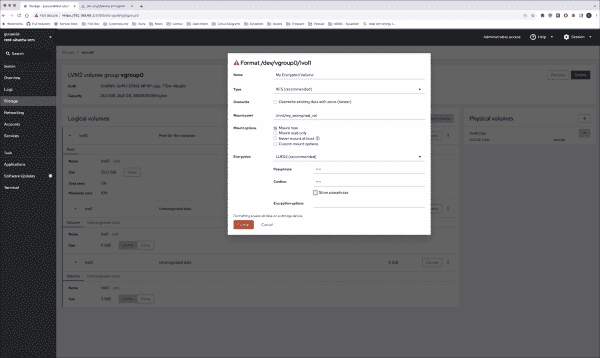
How to Encrypt Linux LVM with Linux Unified Key Setup (LUKS) Using Cockpit
Linux’s logical volume management (LVM) system regulates and apportions data on physical disks. This piece elaborates on LVM’s functioning, methods to manage it on a solo volume, and steps for its encryption through Cockpit. Subsequent articles will delve into the arrangement of your Linux distribution with full-disk encryption, Secure Boot, and TPM2.0 integration (akin to…