Active Directory offers limited authentication choices and, in a majority of companies, the duo of username and password remains to be the main authentication method. Situated in Germany, Systola enhances Active Directory with contemporary authentication methods, all without the need for users to avail of a cloud service.
The frailties of authentication using usernames and passwords are widely-recognized. Microsoft is offering an alternative in the form of certificate-based authentication, typically saved on a smart card. The use of a smart card, in tandem with a PIN, leads to achieving two-factor authentication (“something you have” and “something you know”).
Complex smartcard management
While smart cards provide a secure method for authentication against Active Directory, they are not widely used by many businesses. The key deterrent, particularly for smaller firms, is the attendant administrative burden including certificate renewal and replacement of misplaced smart cards.
Microsoft recommends Azure AD as a solution for companies seeking to implement multi-factor authentication without the use of smart cards. However, Azure AD’s MFA features can only be utilized in a hybrid setting in tandem with the local AD. Additional licensing is necessary for the enhanced security provided by Conditional Access.
Authentication in a modern context without cloud usage
SystoLOCK, created by Systola, offers an alternative approach. This involves the improvement of Active Directory by including different login choices via the integration of a credential authentication service to AD.
Authentication typically occurs through a combination of a PIN and a One-Time Password (OTP). SystoLOCK’s server securely stores the PIN in Active Directory, without requiring any schema extensions.
SystoLock modifies the Windows login screen for entering the PIN and OTP
If the PIN were compromised, it would be useless for attackers on systems, which still accept username and password. In contrast, the theft of an AD password in such cases often has severe consequences.
Token management
PIN-based authentication is further secured by an OTP. SystoLOCK supports both hardware and software tokens. For physical generators, the admin imports a list of keys provided by the device manufacturer into the SystoLock server.
To generate OTP using software tokens, Systola provides an Authenticator app for iOS and Android (SystoLOCK Companion), which operates similarly to Google or Microsoft’s corresponding applications. These apps can also be used with SystoLOCK, although this reduces the available OATH algorithms for OTP generation and other capabilities, such as touchless login and offline login.
Systola provides its own Authenticator app
SystoLOCK Companion can run in a phishing resistant mode where the generated values are not displayed and the entire login process is performed by the app itself.
Companion in phishing resistant mode
Tokens can be generated in the SystoLOCK console with a simple command and assigned to a user account from there. Alternatively, the manufacturer offers numerous PowerShell cmdlets for token management in cases where a large number of tokens need to be generated, deleted, assigned, or reset.
Creating a new token in the SystoLock console
Creating a new token in the SystoLock console
When the admin is in the process of creating a token, they can either instantly assign a PIN or let the user set their own after receiving the token.
As SystoLOCK authentication is enabled, logging in by way of passwords is turned off as a default setting. Although, this can be stopped in the dialog that is used to enter the PIN.
Admins or users can be the ones to assign PINs. In certain scenarios, passwords can also serve as an additional alternative.
Software token configuration
SystoLOCK offers a self-managed method for token supply, removing the necessity for the administrator to generate tokens ahead of time. This can be done by ensuring the relevant accounts are part of an AD group captioned as “SystoLOCK Self-Provisioning Users.”
For those who prefer using a smartphone rather than a physical token, the device registration process is akin to that of Google or Microsoft Authenticator applications. The transfer of the key to the Companion app is conducted via a QR code scanned by the user. Or, users can input their login details and the app will supply the token once it communicates with the server.
SystoLOCK does not compel users to consistently input and read the OTP while logging in. As an alternative, it supports push notifications or QR code login.
There is an available option for the users to save their PIN in the app for their convenience. But, this demands securing the Companion app on the mobile device through methods like Face ID.
Architecture and components
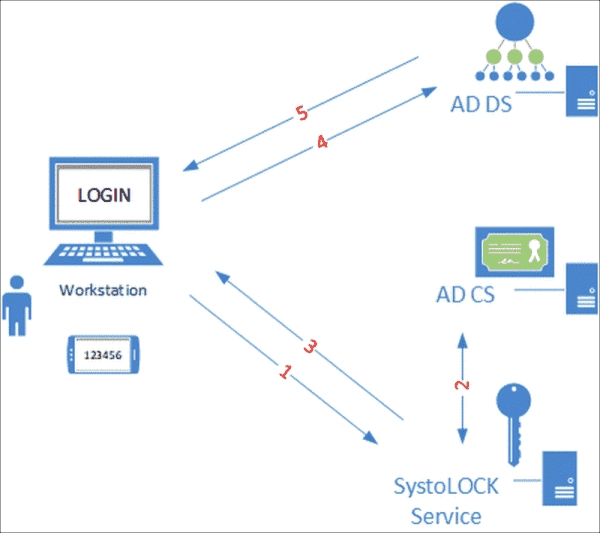
At the core of SystoLOCK is the server module, which verifies login credentials. The manufacturer recommends setting up an instance of this module per domain controller.
The SystoLOCK server requires access to an AD CS certification authority, from which it requests a short-lived certificate (typically 10 minutes) for each login. During installation, it creates its own templates on the CA.
The installation of the SystoLock server adds custom templates to the CA
The installation of the SystoLock server adds custom templates to the CA
The server forwards the certificate to the end device, which then authenticates itself to Active Directory.
Fundamentally, SystoLOCK functions as a smart card infrastructure but adds modern authentication methods to AD through its own server. Furthermore, it eliminates the need for explicit certificate management, as the process is fully automated.
Authentication Workflow with SystoLock Source Systola
The second component is a client module that integrates with Windows’ login infrastructure and replaces the login dialog. By default, it displays fields for username, PIN, and OTP, but it can be configured for other methods like QR codes or push notifications.
If a user has stored their PIN in the Companion app, they can alternatively opt for a QR code being displayed during login, scan it, and log in immediately.
The client software is delivered as an MSI and can be distributed using standard mechanisms like group policies.
Client installation can be done interactively or through MSI distribution via GPO
SystoLOCK management is done through a GUI implemented as an MMC snap-in, which can run side by side with built-in tools like Active Directory Users and Computers or certificate management in the same console.
The SystoLOCK console is based on MMC allowing the integration of additional snap ins.
VPN, Remote Desktop, Office 365
In addition to traditional PC login within the company network, a solution like SystoLOCK must also support other scenarios. This includes users accessing IT resources remotely via RDP or VPN.
The manufacturer facilitates login through RD Web and RD Gateway. In line with VPNs, SystoLOCK is compatible with both the in-built Windows and Cisco AnyConnect client. There is also an NPS plugin available, allowing the integration of any RADIUS compatible VPN solution.
Choosing SystoLOCK over VPN provides a superior advantage to password-based login since users can’t be locked out due to password expiration, hence not interfering with their ability to connect.
Systola extends an adapter for AD FS for enterprises that require federated authentication for Office 365, Salesforce, or other associated SaaS applications.
Offline login
Typically, a network connection for SystoLOCK server validation is required for standard logins. However, with the latest version, you can gain access to your computer even without a network connection. This is only possible with the SystoLOCK Companion.
For computers that may not always have a network connection, you need to enable offline login as it is not set up by default. This can be done by choosing the corresponding option in the SystoLOCK Management Console.
Furthermore, you have the option to allow the computer to support offline login even when the SystoLOCK Companion is not online. This can be done by selecting the Allow Autonomous Login option.
Computers can also be added to specific Active Directory groups or PowerShell can be used to accomplish the same objective.
Once the target computers have registered with the server(s), their status changes from Enabled to Ready, allowing you to log in when they are disconnected from the network.
The SystoLOCK Client will detect offline status and prompt Offline Login. When prompted, the user can scan the QR code from the SystoLOCK Companion and enter their PIN. The SystoLOCK Companion proceeds to access the SystoLOCK Server(s) and provides a response code. This response code should then be entered into the designated field on the user’s computer to finalize the login procedure.
Offline Login with the SystLOCK Companion Source Systola
Summary
SystoLOCK strengthens Active Directory by introducing modern authentication methods, and this is all done without having to integrate with Azure AD in a hybrid configuration. Say goodbye to passwords altogether as this enhances security and provides a convenient user experience when used with the Companion app.
The underlying infrastructure primarily depends on various system services, one of the most essential being a certification authority. Nonetheless, the setup process eases the burden significantly by taking over a significant part of the configuration, including the installation of Certificate Authority, certificate templates, and customizing their permissions.
SystoLOCK, although managing a vital security function, doesn’t embed itself deeply into your system. This minimizes long-term dependencies and allows users to revert to a traditional password-based login by simply uninstalling the client.