Category: Encryption
-
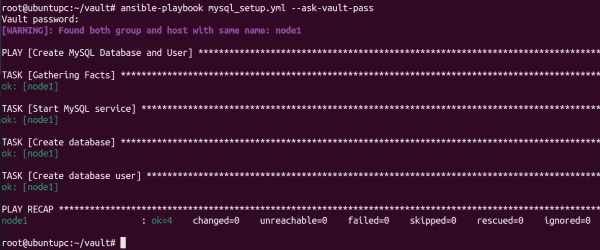
Mastering Encryption and Decryption with Ansible Vault
Ansible Vault allows you to encrypt sensitive data such as passwords, keys, and other secrets rather than storing them as plaintext in your playbooks or roles. In this tutorial, I will explain how to use Ansible Vault to encrypt and decrypt data during playbook runtime. Prerequisites To proceed with this tutorial, you will need the…
-
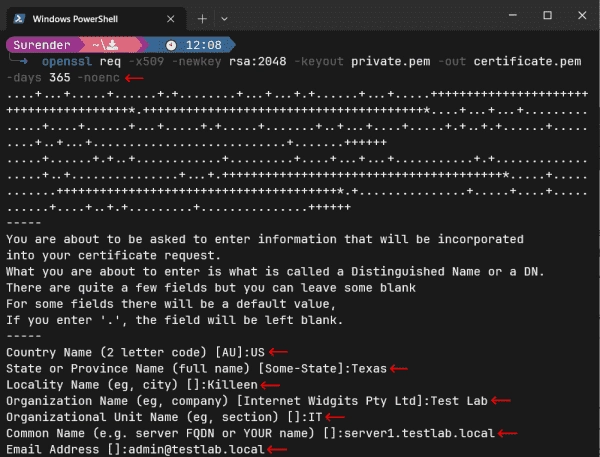
How to Convert Certificate Format Using OpenSSL
OpenSSL is an open-source library and a command-line tool that helps admins and developers perform various cryptographic tasks, such as generating key pairs, certificate signing requests (CSR), verifying certificates, encrypting and decrypting data, identifying certificate information, verifying file integrity and much more. In this post, you will learn how to convert TLS certificates into different…
-
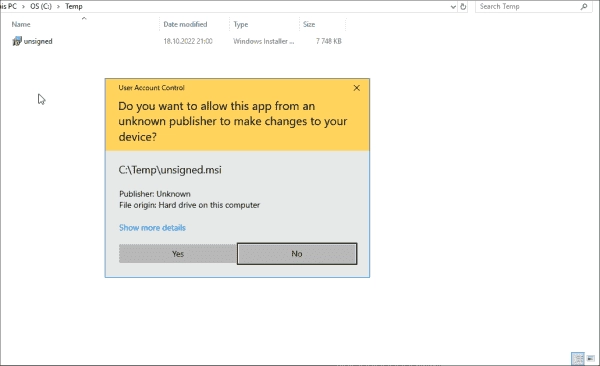
How to Verify Digital File Signatures using SigCheck
SigCheck, part of the SysInternals suite, is a command-line utility offering security features such as verifying the digital file signature and calculating file hashes using multiple hashing algorithms. Distributing digitally signed files to customer computers is a common practice for trusted software publishing companies. The code-signing process uses a certificate from a reliable certification authority…
-
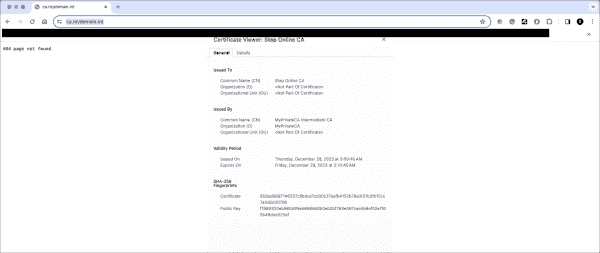
A Guide to Installing and Using the step-ca Certificate Authority Client
The previous article discussed installing an ACME-compatible certificate authority server. This post explains how to install step-cli (ACME client) on a client system to install the new certificate authority (CA), make it trusted, and request a TLS certificate. Install step-cli on a client. Pre-built packages for many operating systems and CPU platforms are on the…
-
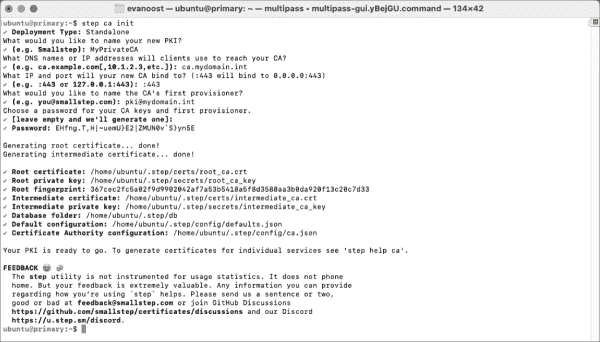
How to Run Your Own Certificate Authority with ACME Support Using Step-ca
Step-ca is a Certificate Authority (CA) management tool for Windows, Linux, and macOS designed to simplify the process of creation, management, and revocation of certificates for use with TLS, mutual TLS (mTLS) authentication, document signing, and other X.509 authentication as well as SSH keys through a variety of provisioners. A provisioner is a method with…
-
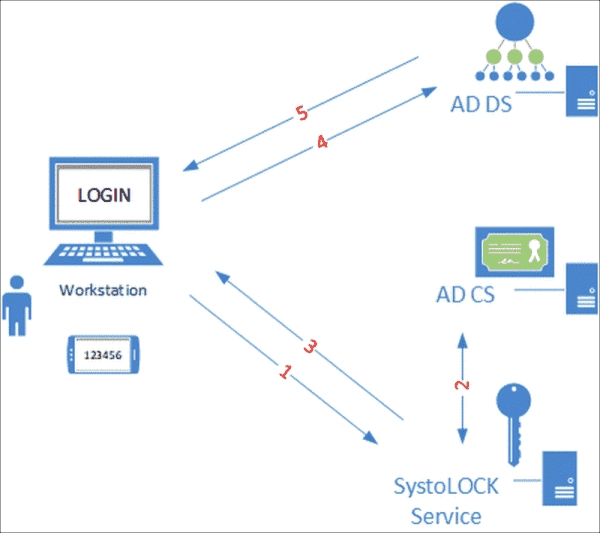
Reviewing SystoLOCK: Multi-Factor Authentication for Active Directory Without Passwords
SystoLOCK presents a sturdy route to boost security using multi-factor authentication (MFA) without requiring passwords in an Active Directory ecosystem. Unlike various other methods, SystoLOCK doesn’t require cloud services. This solution brings about ease similar to smartcard-based authentication, nullifying the requirement for intricate password management. Furthermore, SystoLOCK provides the functionality for users to securely log…
-
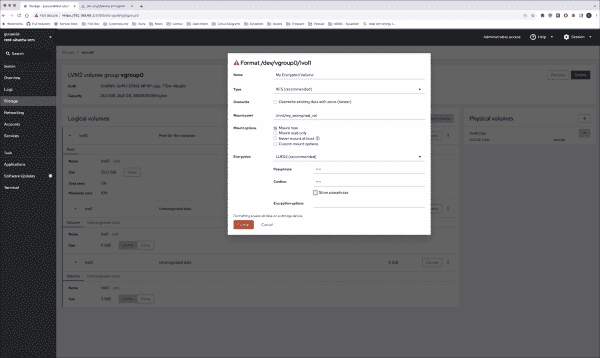
How to Encrypt Linux LVM with Linux Unified Key Setup (LUKS) Using Cockpit
Linux’s logical volume management (LVM) system regulates and apportions data on physical disks. This piece elaborates on LVM’s functioning, methods to manage it on a solo volume, and steps for its encryption through Cockpit. Subsequent articles will delve into the arrangement of your Linux distribution with full-disk encryption, Secure Boot, and TPM2.0 integration (akin to…