Category: Powershell
-

How to Test Your Internet Speed Using Windows Command Prompt and PowerShell
Many online services allow you to test your Internet connection speed in real-time. If you need to regularly collect Internet connection speed metrics from your provider for monitoring, you can use the popular Speedtest console client from Ookla. Let’s look at how to measure the speed of an Internet connection using the Windows command prompt…
-
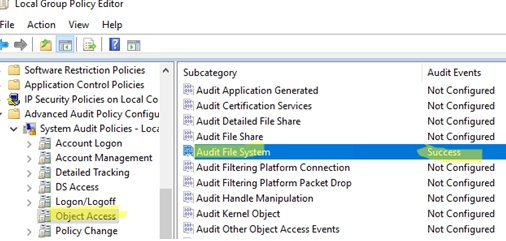
How to Configure File and Folder Access Auditing on Windows Using Group Policy (GPO)
The file system audit policy in Windows allows to monitor all access events to specific files and folders on a disk. An administrator can enable the audit policy to identify file and folder creation, read, modification, and deletion events on the NTFS file system. File system auditing is most commonly used to control access and…
-

Streamline Your Workflow: Adding or Removing Pinned Folders to Quick Access Using PowerShell and GPO
Windows File Explorer has a separate panel that displays a list of favorite folders and locations called Quick Access. Many users and administrators unjustly ignore this handy Windows tool for quickly accessing your favorite folders. This article describes how to use PowerShell and Group Policies to automate the configuration of the Quick Access pane and…
-

Step-by-Step Guide to GPU Passthrough in Hyper-V Virtual Machines
The feature RemoteFX vGPU was previously accessible in older Hyper-V versions (starting from Windows 7 and Windows Server 2008 R2) to allocate a host’s discrete GPU to a virtual machine. However, with the release of Windows 10 version 1809 and Windows Server 2019, the support for RemoteFX was discontinued. The upgraded feature, Discrete Device Assignment…
-
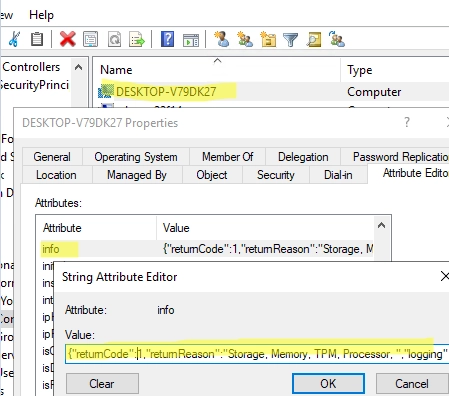
Using PowerShell Script to Assess Windows 11 Hardware Compatibility
In this article, we’ll examine how to employ Microsoft’s official HardwareReadiness.ps1 PowerShell script to run a bulk Windows 11 hardware compatibility check on domain computers. This script ascertains that the computer meets the following minimum criteria to run Windows 11: A compatible x64 processor (complete list of supported CPUs) At least 4 GB of RAM…
-
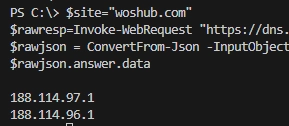
Guide to Reading, Modifying, and Parsing JSON Files with PowerShell
JSON is a popular text-based format for representing and transmitting structured data based on JavaScript object syntax. There are two cmdlets in PowerShell that allow you to work with the JSON data format: ConvertFrom-Json and ConvertTo-Json. Let’s look at how you can use PowerShell to create, read, or modify JSON objects and save them to…
-
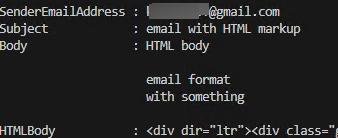
A Comprehensive Guide on How to Use PowerShell to Read Outlook Emails
Let’s examine the process of opening, reading, and parsing emails from a connected Outlook mailbox using a PowerShell script. The direct access to the mailbox is facilitated by Outlook MAPI, which not only lists the mailbox items, but enables you to read the emails, including details such as the sender’s address, subject, and body among…
-
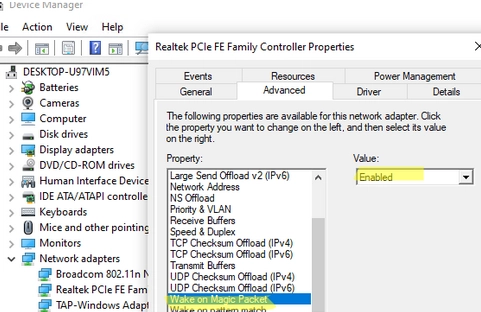
Step-by-step Guide to Enabling and Configuring Wake-on-LAN (WoL) in Windows
Wake on LAN (WoL) is an essential feature in computer networking that allows a device in sleep mode or low power mode to be remotely activated. This is made possible through the device’s network interface card (NIC), which prompts the computer to wake up anytime it receives a unique broadcast packet, often referred to as…
-
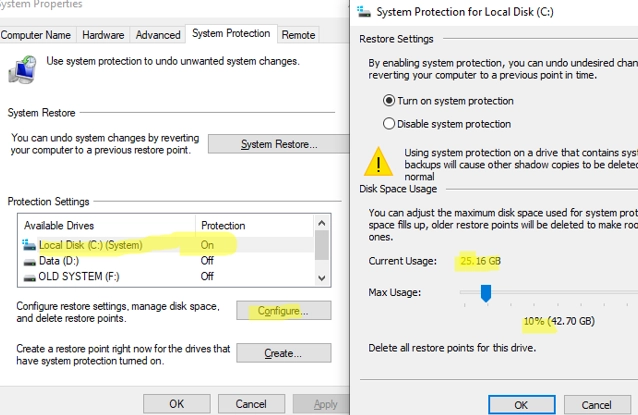
A Comprehensive Guide on Creating, Deleting and Managing System Restore Points on Windows 10/11
System Restore Points offer a convenient solution for reverting your Windows OS to a previous state should you encounter unintended system file or registry issues following the installation of faulty drivers, updates, or applications. A restore point allows you to restore the state of the registry, system files, drivers, and installed software to the point…
-
Step-by-step Guide: How to Add an ESXi Host to VMware vCenter Server (vCSA)
Let’s examine how to incorporate a standalone host with an ESXi hypervisor into the VMware vCenter Server (vCSA) for administrative centralization and utilization in cluster setups. Establish a connection to the vCenter Server by launching the vSphere Client URL in your internet browser (https://vcenter_server_fqdg_or_ip/ui). Choose the datacenter, folder, or cluster where you intend to introduce…