Category: Linux
-
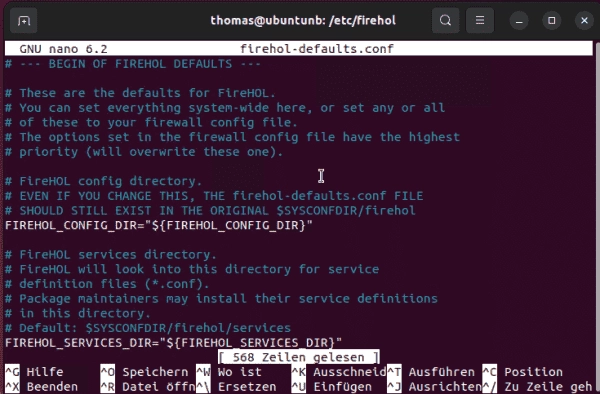
How to Configure iptables Using Firehol: A Comprehensive Guide
Firehol is an open-source tool used to configure Linux firewalls, such as those based on iptables. Advanced users can delve deeper into the rule set with optional parameters. Firehol ensures that the rules are coherent in both directions. By default, Firehol generates rules for both IPv4 and IPv6. This can be changed in the configuration…
-
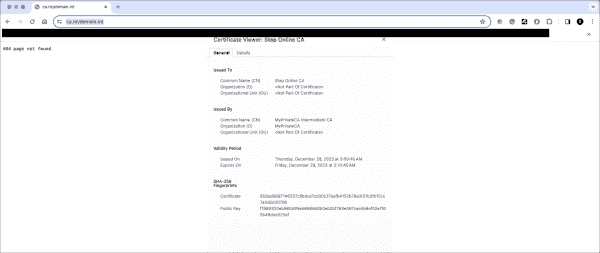
A Guide to Installing and Using the step-ca Certificate Authority Client
The previous article discussed installing an ACME-compatible certificate authority server. This post explains how to install step-cli (ACME client) on a client system to install the new certificate authority (CA), make it trusted, and request a TLS certificate. Install step-cli on a client. Pre-built packages for many operating systems and CPU platforms are on the…
-
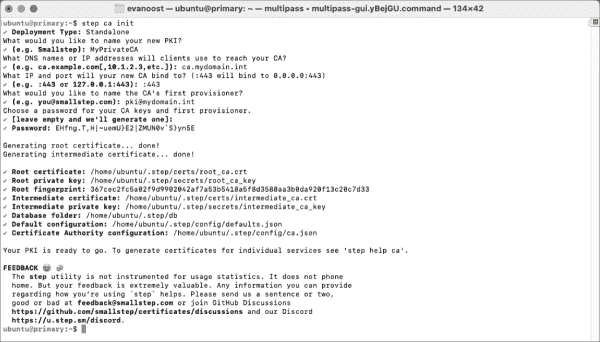
How to Run Your Own Certificate Authority with ACME Support Using Step-ca
Step-ca is a Certificate Authority (CA) management tool for Windows, Linux, and macOS designed to simplify the process of creation, management, and revocation of certificates for use with TLS, mutual TLS (mTLS) authentication, document signing, and other X.509 authentication as well as SSH keys through a variety of provisioners. A provisioner is a method with…
-
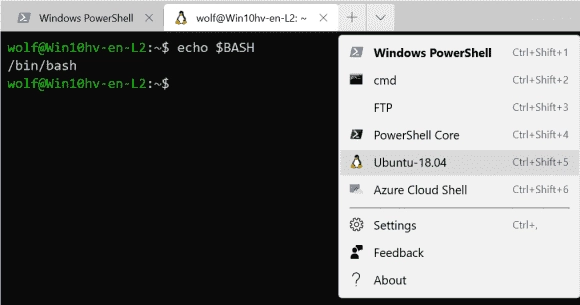
A Comprehensive Guide to Installing Windows Subsystem for Linux (WSL) on Various Windows Editions and Server Core
For some time now, Microsoft has been offering a simplified installation of WSL via the wsl.exe utility. Hence, most guides refer to this method. However, in practice, it is not quite as straightforward because this command does not work on Server Core and is only suitable for WSL 2. Ideally, the Windows Subsystem should be…
-
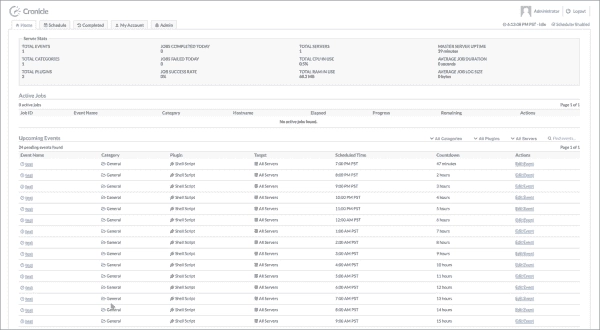
A Comprehensive Guide to Installing Cronicle Task Scheduler with Nginx Proxy
Cronicle is a web-based, multi-server task scheduling and automation platform designed to handle complex job scheduling and workflow management across multiple servers. It offers a user-friendly interface for creating, managing, and monitoring tasks, supporting a wide range of job types, including shell scripts, commands, and custom plugins. With features like real-time logging, error notification, and…
-
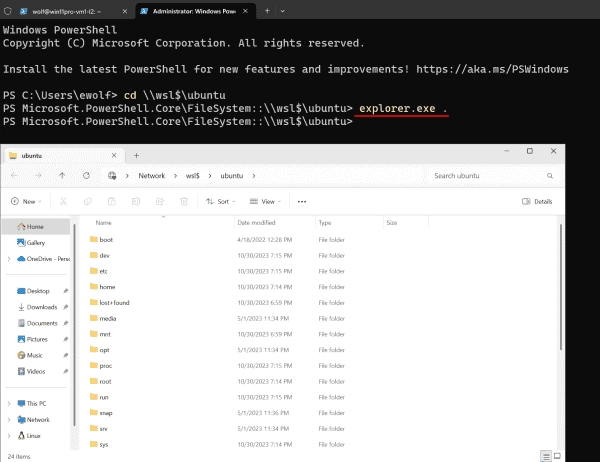
Utilizing WSL: How to Launch Linux Apps on Windows and Windows Apps on Linux, and Access Ext4 and NTFS
The Windows Subsystem for Linux (WSL) strives to unite the open-source operating system with Windows, diminishing the distinction for users between the two. A significant part of this effort is the capacity to interact with either operating system’s file system and launch programs from either system. Looking from a technical perspective, WSL 2 employs a…
-
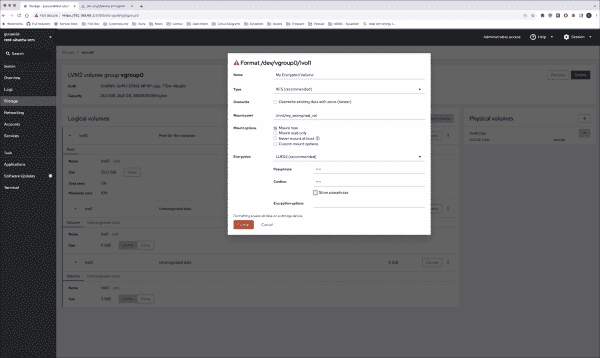
How to Encrypt Linux LVM with Linux Unified Key Setup (LUKS) Using Cockpit
Linux’s logical volume management (LVM) system regulates and apportions data on physical disks. This piece elaborates on LVM’s functioning, methods to manage it on a solo volume, and steps for its encryption through Cockpit. Subsequent articles will delve into the arrangement of your Linux distribution with full-disk encryption, Secure Boot, and TPM2.0 integration (akin to…