-

Microsoft Announces Update Separation for Windows 11 and Server 2025
Microsoft plans to streamline future updates for its operating systems by separating the updates for Windows 11 and Windows Server 2025. Beginning January 13, 2026, each update will be assigned distinct KB numbers, allowing for clearer documentation and the possibility of tailored update packages for desktop or server systems. This change was first hinted at…
-

Upcoming End-of-Support Wave: Microsoft to Bid Farewell to Windows 11 24H2, Office 2021, and More in 2026
Microsoft has announced plans to discontinue support for several of its products in 2026, including Windows 11 24H2. As Windows 11 approaches its five-year anniversary, the upcoming support cuts are significant. The end of support for Windows 11 24H2 is scheduled for October 4, 2026, which means after this date, Microsoft will halt the release…
-

Unlocking Enhanced Performance: Windows 11 PC Upgrade at No Cost!
Microsoft has recently released a native NVMe SSD performance driver for Windows Server 2025, which has sparked interest as users have discovered a method to enable the same feature on Windows 11 through registry modifications without any cost. Initial benchmarks indicate significant performance enhancements, especially for consumer PCs and portable gaming devices, particularly in random…
-
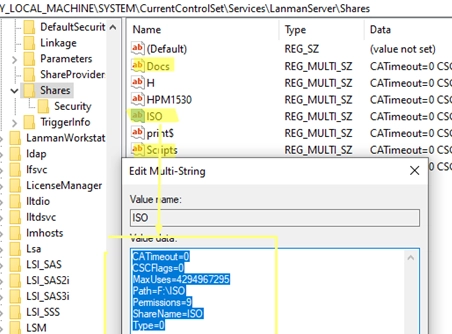
A Step-by-Step Guide to Migrating Your Existing Windows Shares to a New File Server
To migrate existing Windows shares to a new file server, you’ll need to utilize a combination of registry editing and file transfer methods. The shared network folders and their settings are stored under HKLMSYSTEMCurrentControlSetServicesLanmanServerShares in the Windows registry. Step-by-Step Guide for Migration: List Existing Shares:To view current shared SMB resources on a Windows host, use…
-

Microsoft’s “Storage Revolution”: Native NVMe Support Arrives in Windows Server 2025
Microsoft has announced the inclusion of native NVMe support in Windows Server 2025, which the company heralds as a "storage revolution." This development is anticipated to bring significant performance enhancements, particularly for enterprise applications. By implementing native NVMe, Windows Server 2025 can unlock the full potential of modern NVMe devices including PCIe Gen5 SSDs, delivering…
-
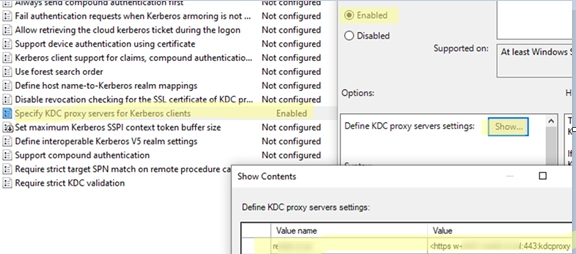
Leveraging KDC (Kerberos) Proxy in Active Directory for Secure Remote Access
The Kerberos Key Distribution Center (KDC) proxy service is designed to provide a secure way for remote clients to authenticate using Kerberos when they cannot access Active Directory domain controllers directly. Initially intended for services like DirectAccess and Remote Desktop Gateway, the KDC proxy becomes increasingly important as Microsoft phases out NTLM authentication protocols, necessitating…
-
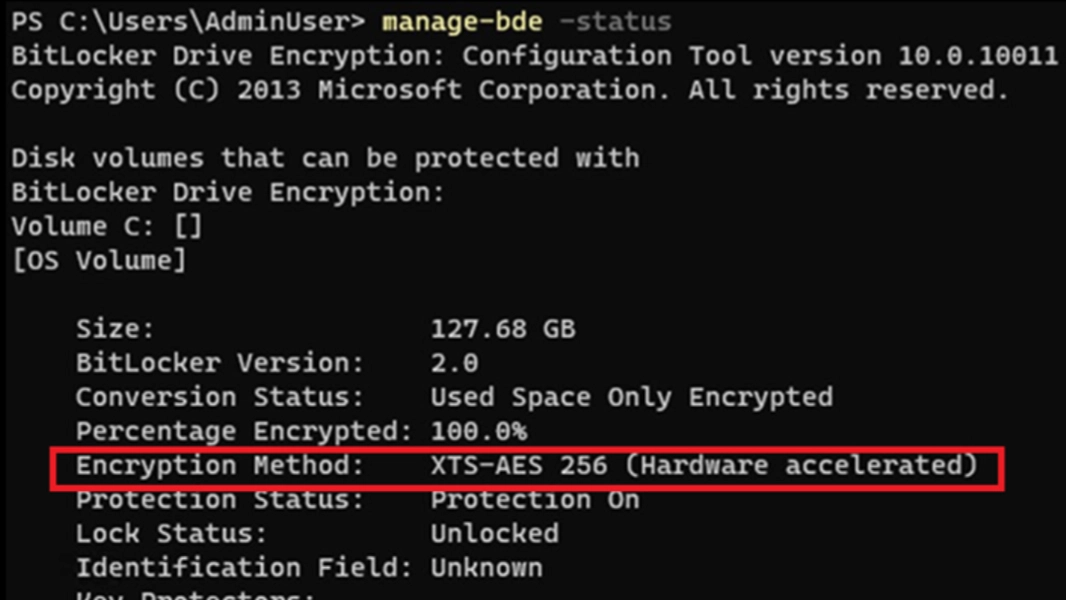
Microsoft Introduces Hardware-Accelerated BitLocker in Windows 11 25H2: What You Need to Know
Microsoft has introduced hardware-accelerated BitLocker capabilities with the latest update of Windows 11 (25H2) and Windows Server 2025, a move that aligns with the performance improvements seen in modern SSD technologies. According to Microsoft’s Rafal Sosnowski, the evolution of Non-Volatile Memory Express (NVMe) drives facilitates incredibly fast data transfer rates but also poses a challenge,…
-

SSD Afterburner: Introducing Microsoft’s New NVMe Driver for Windows 11
Microsoft has introduced a new NVMe driver for Windows Server 2025 to enhance SSD performance, which is also included in Windows 11. This update promises to significantly boost Input/Output Operations Per Second (IOPS) and overall data throughput while reducing CPU load. The previous driver setup posed a bottleneck because Windows converted NVMe commands to the…
-
Microsoft’s Bold Initiative: Enhancing SSD Performance on Windows Systems
Microsoft is making significant strides to enhance SSD performance in its upcoming Windows Server 2025, with hopes of integrating these improvements into Windows 11. The tech giant is modernizing how its operating systems manage read and write commands for storage devices, specifically targeting high-end SSDs that connect via PCI Express. Historically, Windows has limited support…
-

Step-by-Step Guide to Manually Create and Install a Windows Service
In Windows, services operate in the background, allowing applications to run without user interaction and start automatically during boot. This guide walks you through the process of creating a new system service from an executable file using built-in tools available in Windows. To create a service, you can utilize the sc.exe command from the command…