One primary benefit of SMB over QUIC is its outstanding performance when reaching file shares. Nevertheless, it also amplifies the safety of file services by acting as an SMB VPN for remote users. The SMB traffic, including authentication, is directed through a TLS 1.3-encrypted tunnel.
Despite Microsoft’s claim that SMB over QUIC is the future, traditional transport methods will remain. Windows Server introduces numerous features to enhance their security too.
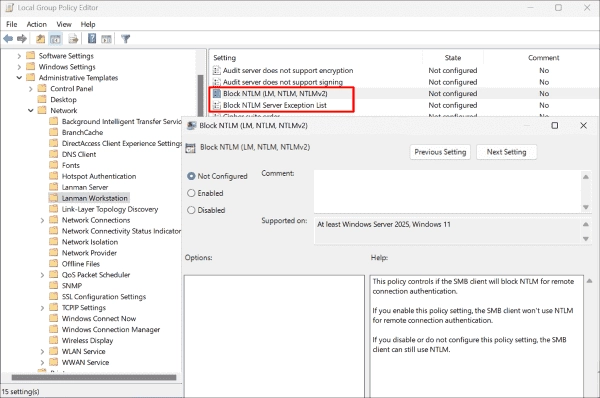
Block NTLM authentication for SMB connections
Clients and servers default to negotiating the authentication protocol by means of SPNEGO. As a rule, Kerberos is employed for interactions between domain-joined machines.
There are unique situations where NTLM authentication is required, such as:
- if the client sets up a connection using an IP address;
- if the Kerberos CIFS Service Principal Name for the SMB server isn’t found in the Active Directory;
- or if a local user account is involved in logging into the SMB server.
In the intermediate and long run, Kerberos extensions will bypass the need for NTLM authentication. Until then, Microsoft offers the feature to disable NTLM for SMB. However, if NTLM must be used due to the above-mentioned circumstances, connections will inevitably fail.
Blocking via Group Policy
Windows 11 and Server 2025 have introduced a Group Policy named Block NTLM (LM, NTLM, NTLMv2) for this purpose. This policy is specific to the SMB client and can be located under Computer Configuration > Policies > Administrative Templates > Network > Lanman Workstation.
For servers that depend on NTLM authentication, exceptions for them can be defined. The group policy Block NTLM Server Exception List is designed for this purpose.
Restrict NTLM authentication using PowerShell
In addition, it is possible to disable NTLM with PowerShell for all or specific SMB servers:
Set-SMbClientConfiguration -BlockNTLM $true
This command globally changes the configuration of the SMB client. To narrow the scope to a specific connection, use the following:
New-SmbMapping -RemotePath \servershare -BlockNTLM $true
The current status of this property can then be queried with
Get-SMbClientConfiguration | select BlockNTLM
and
Get-SmbMapping | select BlockNTLM
Even the traditional net use command now employs a /blockntlm switch.
Restrict the quantity of NTLM login attempts
In the case that intruders are successful in speculating usernames or retrieving them from the Active Directory, they have the ability to transmit NTLM login trials to an SMB server at considerably brief intervals.
Generally, lists or dictionaries of compromised passwords are employed in attempts to guess the passwords of the accounts being targeted. With automated attacks, where hundreds of login attempts can be made per second, the probability of a successful authentication within a short time increases significantly.
In the past, corporations have been able to guard against this by disabling accounts following a specific number of unsuccessful login attempts. Nevertheless, this feature can be manipulated for denial-of-service attacks.
Intervals between logins
An alternative safeguarding mechanism against abusive SMB NTLM authentications is introduced with Windows Server 2025. The ‘SMB NTLM Authentication Rate Limiter’ sets intervals that need to pass between two login attempts. This can be used, for instance, when the blocking of SMB NTLM is not viable.
This feature slows down automated attacks, significantly extending the time to hack a password.
Configuration via Group Policy
The Enable Authentication Rate Limiter policy can reduce the number of login attempts within a specific interval. This setting is found under LanMan Server.
Throttle logon attempts and brute force attacks via Group Policy.
Throttle logon attempts and brute force attacks via Group Policy.
However, the Group Policy does not allow the configuration of intervals between invalid login attempts; this can only be done with PowerShell.
Administration via PowerShell
To query the current setting in PowerShell, use the following command:
Get-SmbServerConfiguration | select InvalidAuthenticationDelayTimeInMs
To set the interval between two login attempts, run this command:
Set-SmbServerConfiguration -InvalidAuthenticationDelayTimeInMs <milliseconds>
Enforce specific SMB versions
By default, SMB clients and servers negotiate the highest protocol version supported by both sides. With two new Group Policy settings, administrators can now set a minimum and maximum version of SMB.
This means that you can block older and less secure versions. The lowest available version is 2.0.2. For example, if an organization sets the policy to the latest version, 3.1.1, all previous versions are no longer allowed.
The Group Policy for setting a minimum and maximum SMB version exists for both the client (outgoing connection) and the server (incoming connection). It can be found under Computer Configuration > Policies > Administrative Templates > Network > LanMan Workstation or LanMan Server.
Selecting the minimum and maximum SMB versions using Group Policy settings
Microsoft provides the option to modify settings through PowerShell. The following cmdlets can be used:
- Set-SmbClientConfiguration
- Set-SmbServerConfiguration
These cmdlets support the parameters: Smb2DialectMin and Smb2DialectMax. Similarly to the Group Policy setting, you can use SMB202 to SMB311 as values.
To display the existing settings, you can use Get-SmbClientConfiguration and Get-SmbServerConfiguration.
As the above screenshot shows, all SMB versions are allowed by default.
SMB signing enabled by default
Previously, only connections to a domain controller required SMB signatures. Microsoft will enable SMB signing by default for both the client and the server.
The decision was delayed due to potential compatibility issues with older systems. Administrators should, therefore, prepare for this upcoming change.
The following PowerShell commands can be used to query the current client and server settings for SMB signing:
Get-SmbClientConfiguration | Format-List RequireSecuritySignatureGet-SmbServerConfiguration | Format-List RequireSecuritySignature
Until now, SMB signing has been disabled by default.
Until now, SMB signing has been disabled by default.
Disable SMB signing
If a legacy system does not support SMB signing, it can be disabled for outgoing client connections using the following PowerShell command in an elevated PowerShell session:
Set-SmbClientConfiguration -RequireSecuritySignature $false
To disable the SMB signature request on the server, use the following PowerShell command:
Set-SmbServerConfiguration -RequireSecuritySignature $false
There are also settings in Group Policy for this task, named Microsoft Network (Client/Server): Communication digitally sign. These settings exist for the client and server with the options always or “if the other party agrees.”
They can be found under Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options.