If you suspect that the built-in Windows Defender Firewall is obstructing network connections from a specific program or service, it’s unwise to disable it entirely. Instead, you can log all network traffic passing through the firewall to identify filtered or dropped packets, as well as find relevant ports and source/destination IP addresses. This will allow you to create appropriate allow rules.
Enable Logging in Windows Firewall
Windows Defender Firewall can log both successful and blocked network connections. You can enable logging for each network profile (Private, Public, or Domain). By default, traffic logging is disabled. Follow these steps to activate it:
- Open Windows Firewall with Advanced Security MMC (
wf.msc). - Right-click on the console’s root and select Properties.
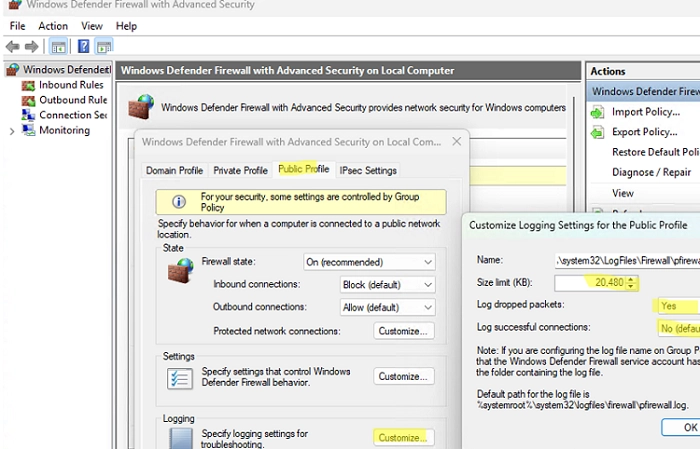
- Navigate to the desired network profile tab (Domain, Private, or Public) that you wish to configure.
- Click the Customize button in the Logging section.
- Modify the following settings as needed:
- Log file name: Default is
%systemroot%system32LogFilesFirewallpfirewall.log. - Size limit: Increase from 4 MB to up to 20 MB (
20480KB). - Log dropped packets: Choose whether to log dropped connections.
- Log successful connections: Be aware that logging all successful connections may create large log files.
- Log file name: Default is
You can also configure logging options via PowerShell using commands like:
Set-NetFireWallProfile -Profile Public -LogBlocked True -LogMaxSize 20480 -LogFileName "%systemroot%system32LogFilesFirewallpfirewall.log" -VerboseParsing Windows Firewall Logs with PowerShell
With logging enabled, all network connections are recorded in a plain text file, which you can search using PowerShell. For instance, to view filtered connections to TCP port 445, use the following command:
Get-Content C:WindowsSystem32LogFilesFirewallpfirewall.log -wait | Select-String -pattern "DROP.*TCP.*445"A typical log entry format is:
date time action protocol src-ip dst-ip src-port dst-port size tcpflags tcpsyn tcpack tcpwin icmptype icmpcode info path pidA PowerShell function can help visualize the log data:
function Get-WindowsFirewallLog { param( [parameter(Position=0,Mandatory=$false)] [ValidateScript({Test-Path $_})] [string]$LogFilePath = "$env:SystemRootSystem32LogFilesFirewallpfirewall.log" ) $headerFields = @("date","time", "action","protocol","src-ip","dst-ip","src-port","dst-port","size", "tcpflags","tcpsyn", "tcpack","tcpwin","icmptype","icmpcode", "info","path") $firewallLogs = Get-Content $LogFilePath | ConvertFrom-Csv -Header $headerFields -Delimiter ' ' $firewallLogs | Out-GridView}View Windows Firewall Logs in Event Viewer
Alternatively, you might consider writing Windows Firewall connection logs to the Event Viewer for easier access. This requires enabling certain audit policies in the local Group Policy Object (GPO):
- Open the local GPO editor (
gpedit.msc). - Navigate to Computer Configuration -> Windows Settings -> Security Settings -> Advanced Audit Policy Configuration -> System Audit Policies.
- Enable the Audit Filtering Platform Packet Drop policy to log blocked connections.
You can view Windows Firewall events in the Event Viewer (eventvwr.msc). Look for events with EventID 5152, which signify blocked packets, and find details like protocol, IP address, and process name.
Using the Get-WinEvent PowerShell cmdlet, you can filter these firewall events programmatically:
$destinationPort = "3388"$filterXml = @"<QueryList> <Query Id="0" Path="Security"> <Select Path="Security"> *[System[(EventID=5152)]] and *[EventData[Data[@Name='DestPort'] and (Data='$destinationPort')]] </Select> </Query></QueryList>"@$events = Get-WinEvent -FilterXml $filterXmlEnabling logging for the Windows Firewall allows you to monitor both allowed and blocked connections, assisting in the identification of issues with your firewall rules and enabling effective troubleshooting. For further guidance on managing Windows Firewall, visit this link.