Category: Articles
-
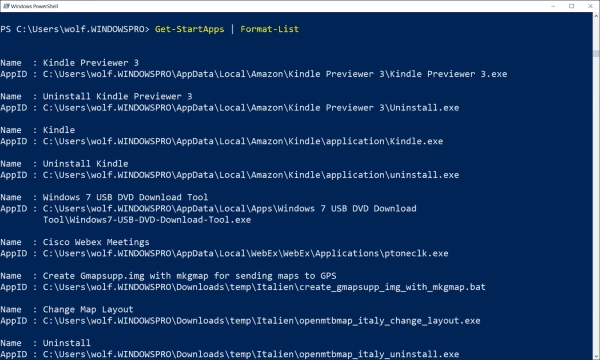
Tailoring and Implementing the Windows 11 Taskbar: A Guide on Using GPO or Intune
Organizations have the ability to control the look of the Windows taskbar on every networked computer, mainly by pinning vital applications. Administrators achieve this by setting up the applications in an XML file that is then distributed to each terminal using GPO or Microsoft Intune. Pinning important company applications isn’t the only reason for taskbar…
-
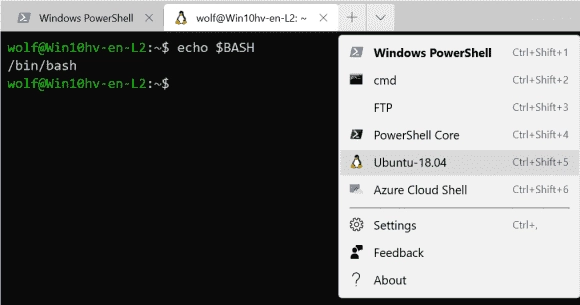
A Comprehensive Guide to Installing Windows Subsystem for Linux (WSL) on Various Windows Editions and Server Core
For some time now, Microsoft has been offering a simplified installation of WSL via the wsl.exe utility. Hence, most guides refer to this method. However, in practice, it is not quite as straightforward because this command does not work on Server Core and is only suitable for WSL 2. Ideally, the Windows Subsystem should be…
-
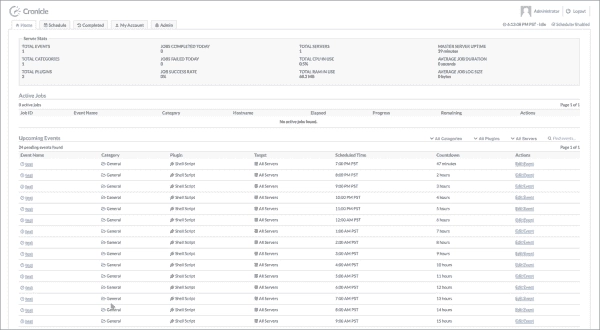
A Comprehensive Guide to Installing Cronicle Task Scheduler with Nginx Proxy
Cronicle is a web-based, multi-server task scheduling and automation platform designed to handle complex job scheduling and workflow management across multiple servers. It offers a user-friendly interface for creating, managing, and monitoring tasks, supporting a wide range of job types, including shell scripts, commands, and custom plugins. With features like real-time logging, error notification, and…
-
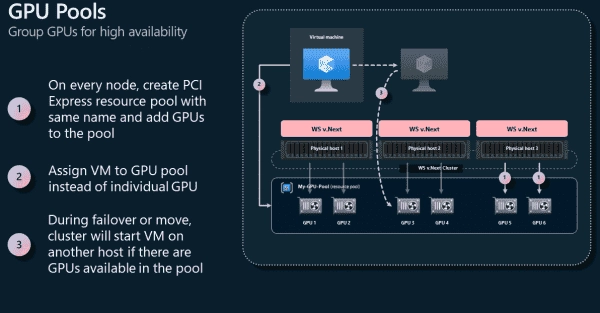
Exploring Features of Windows Server 2025 Hyper-V: GPU Partitioning, VHDs Deduplication, and AD-less Live Migration
The upcoming LTSC release of Windows Server introduces several enhancements to Hyper-V and new storage functions, which primarily benefit the operation of virtual machines. This includes GPU virtualization, a new deduplication feature for ReFS, and live migration of VMs on clusters that are not members of an AD domain. As hypervisors have matured, there haven’t…
-
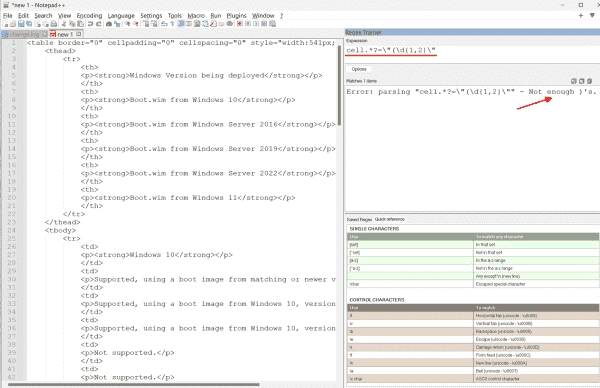
Mastering Notepad++: Exploring Search, Replace Functions with Regex and Plugins
The free and widely-used editor for Windows supports not only basic search and replace functions but also regular expressions. A helpful plugin assists in formulating regex, providing real-time expression validation. However, for many tasks you don’t need regex; built-in functions and plugins often offer simpler solutions. The raw output of scripts is often extensive and…
-
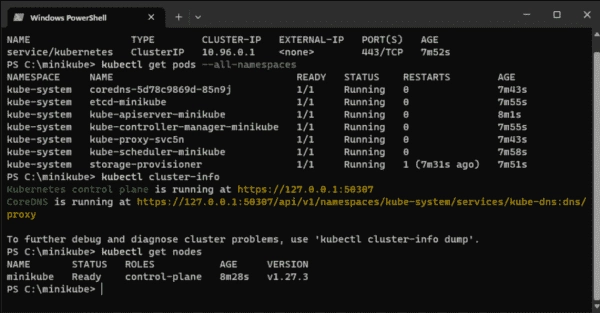
Step-by-Step Guide to Installing Minikube on Windows
Minikube is an ideal solution for setting up a Kubernetes cluster for a test or development environment. It only requires a single node, optionally as a virtual machine. To install Minikube on Windows, several preparations are required, including the installation of Docker. The first step to install Kubernetes on Windows 10/11 or Windows Server 2019/2022…
-
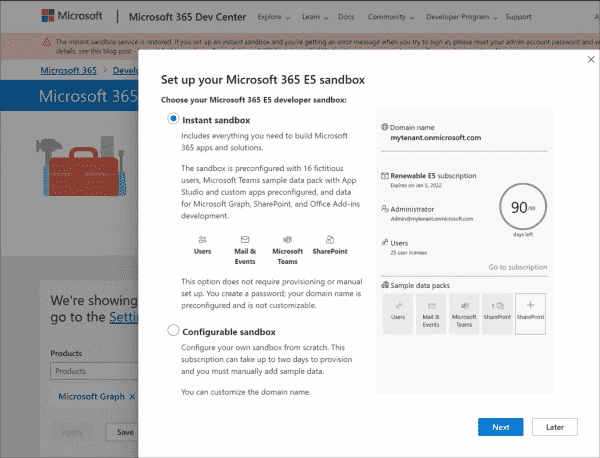
Step-by-Step Guide to Creating a Free Lab for Microsoft 365 and Intune
If you’re looking to delve into Microsoft 365 management, there are a few options available. Some components offer free, time-limited trial versions, and in the case of Azure AD, there’s a stripped-down free edition. Alternatively, Microsoft provides a developer license with a fully-featured subscription to M365 E5. If you aim to further your knowledge of…
-
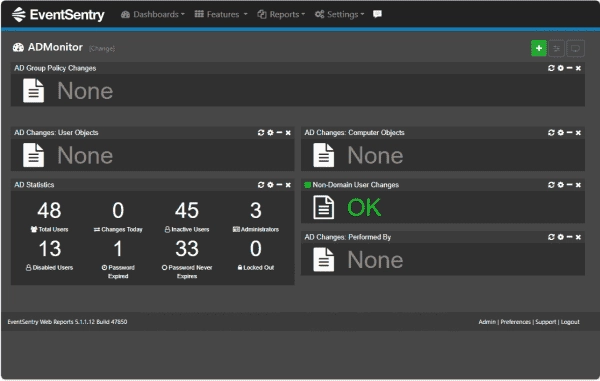
Unveiling EventSentry 5.1: Exploring its New Network Security Monitoring and Compliance Features
Explore the new features in EventSentry 5.1, including anomaly detection, NTFS permissions inventory, and new compliance dashboards. Many log collection and SIEM solutions are available in the market today. A notable solution in this space is EventSentry. EventSentry 5.1 is a recent release that brings numerous enhancements to the platform. Brief overview of EventSentry EventSentry,…
-
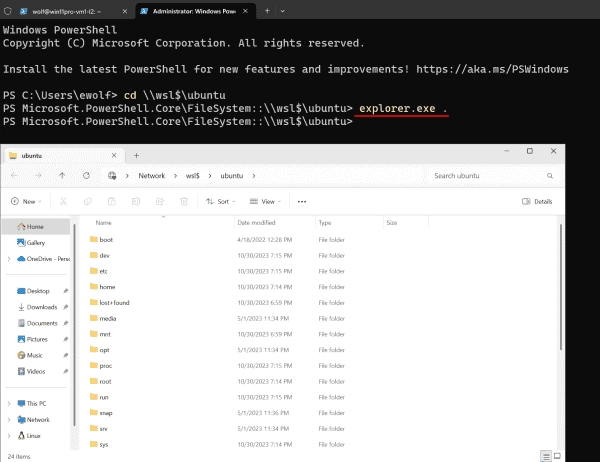
Utilizing WSL: How to Launch Linux Apps on Windows and Windows Apps on Linux, and Access Ext4 and NTFS
The Windows Subsystem for Linux (WSL) strives to unite the open-source operating system with Windows, diminishing the distinction for users between the two. A significant part of this effort is the capacity to interact with either operating system’s file system and launch programs from either system. Looking from a technical perspective, WSL 2 employs a…
-
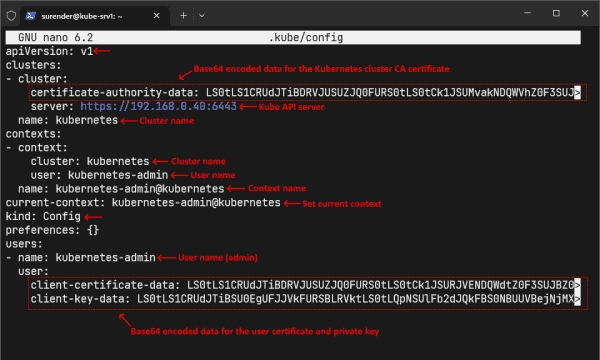
Understanding Role-Based Access Control (RBAC) in Kubernetes
In a previous post in this Kubernetes guide, you learned about deploying stateful applications with Kubernetes StatefulSets. Today, we will discuss role-based access control (RBAC) in Kubernetes, which controls who can access Kubernetes cluster resources. It uses roles and role bindings to grant permissions to subjects, such as users, groups, or service accounts. Verify Kubernetes…