Category: Articles
-
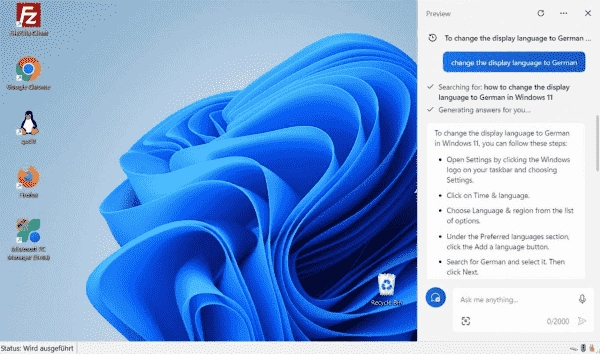
Steps to Disable Copilot and Block ChatGPT on Windows and Edge Using Group Policy and Defender
Microsoft has integrated AI features under the brand Copilot into almost all of its products, including Windows and the Edge browser. For businesses that haven’t developed an AI strategy yet, these consumer versions of Copilot are often undesired. Fortunately, they can be blocked using group policies. In principle, the potential of generative AI for many…
-
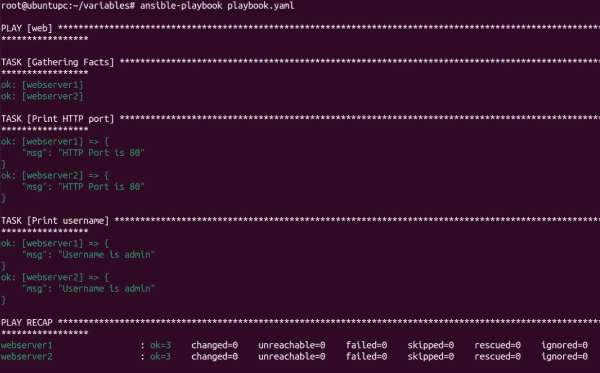
Mastering Ansible Variables: A Guide with Practical Examples
Ansible variables store and manipulate data that can be accessed and utilized across playbooks, roles, and tasks. They allow for dynamic configurations and flexible automation by enabling the abstraction of values that may change based on different environments or use cases. In this tutorial, I will introduce Ansible variables and explore their usage with examples.…
-
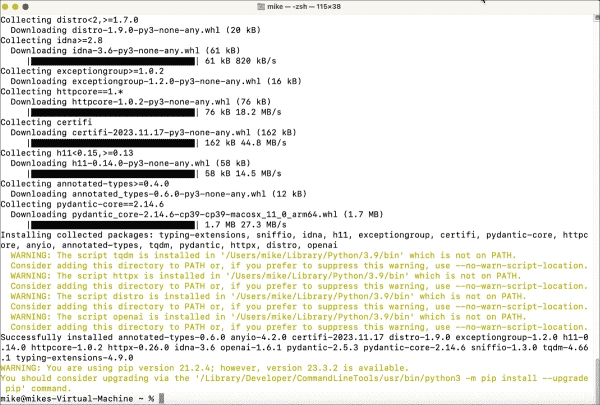
Step-by-Step Guide to Installing Python OpenAI SDK on Windows and macOS
2024 will most likely be the year when many admins will be faced with deploying AI systems for the first time. Once you play a little with the OpenAI API, you will begin to understand why Large Language Models (LLMs) are not just useful for chatbots. If AI companies can find a way to fund…
-
Unveiling Hypocrisy: A Review of OpenAI’s Controversial Article in The New York Times
OpenAI is nervous. Very nervous. Their latest blog post is proof. They have realized that the ongoing lawsuit with the New York Times poses a significant threat to their entire business model. Their belief that they could freely harvest the content of the entire internet for training their AI models was, in fact, quite naive.…
-
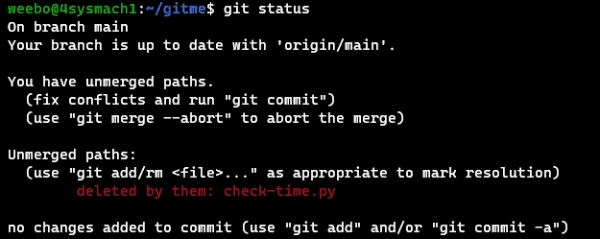
Steps to Resolve Merge Conflicts in Git: Dealing with Modify/Delete Issues
In my previous article, I discussed merge conflicts, specifically line merge conflicts, and how to resolve them on GitHub. In this article, I will focus on another type of merge conflict, the modify/delete conflict, and how to resolve it using Git. Modify/delete conflicts occur when, on one branch in the merge operation, a file has…
-
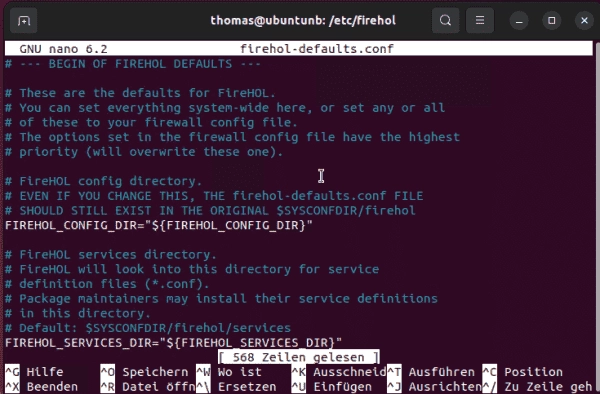
How to Configure iptables Using Firehol: A Comprehensive Guide
Firehol is an open-source tool used to configure Linux firewalls, such as those based on iptables. Advanced users can delve deeper into the rule set with optional parameters. Firehol ensures that the rules are coherent in both directions. By default, Firehol generates rules for both IPv4 and IPv6. This can be changed in the configuration…
-
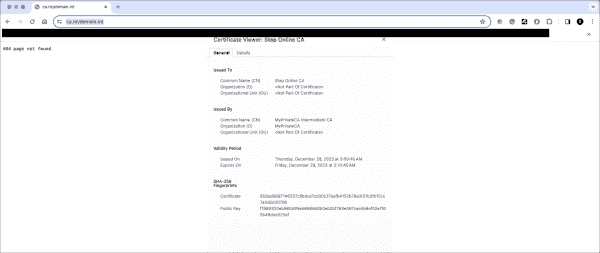
A Guide to Installing and Using the step-ca Certificate Authority Client
The previous article discussed installing an ACME-compatible certificate authority server. This post explains how to install step-cli (ACME client) on a client system to install the new certificate authority (CA), make it trusted, and request a TLS certificate. Install step-cli on a client. Pre-built packages for many operating systems and CPU platforms are on the…
-
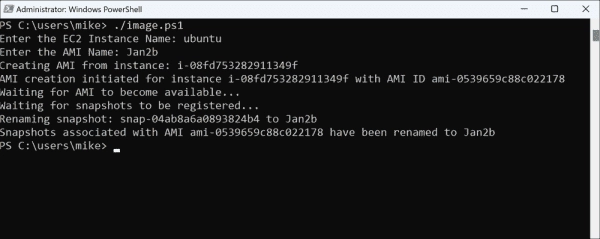
Step-by-Step Guide on Creating an Amazon Machine Image (AMI) for an EC2 Instance using Bash and PowerShell Scripts
The provided Bash and PowerShell script helps automate the creation of Amazon Machine Images (AMIs) from existing AWS Elastic Compute Cloud (EC2) instances. This is particularly useful for creating point-in-time backups or disaster recovery. I mostly use the script to quickly clone an EC2 instance for testing or troubleshooting. Create an AMI in the AWS…
-
Review: Achieving Mastery over Outlook Data Files with Stellar Toolkit for Outlook
The Stellar Toolkit for Outlook is a comprehensive suite of tools designed to manage and optimize the performance of Microsoft Outlook. It includes various functionalities such as repairing PST files, recovering lost or deleted emails, merging PST files, and converting OST files to PST format. Additionally, it offers features to remove duplicate emails and compact…
-
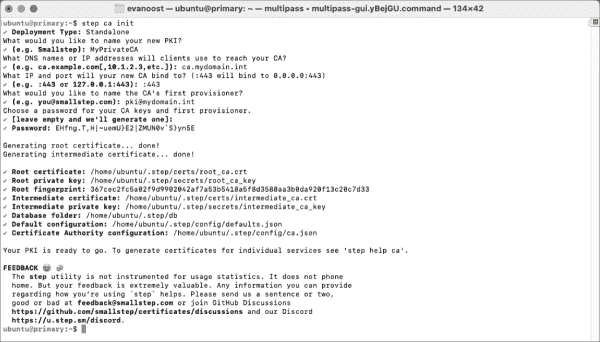
How to Run Your Own Certificate Authority with ACME Support Using Step-ca
Step-ca is a Certificate Authority (CA) management tool for Windows, Linux, and macOS designed to simplify the process of creation, management, and revocation of certificates for use with TLS, mutual TLS (mTLS) authentication, document signing, and other X.509 authentication as well as SSH keys through a variety of provisioners. A provisioner is a method with…