A major advantage of QUIC is its mandatory certificate-based encryption. SMB over QUIC is like an SMB VPN for users working remotely. The server certificate creates a TLS 1.3 encrypted tunnel via UDP port 443. SMB traffic, including authentication, is not exposed to the underlying network.
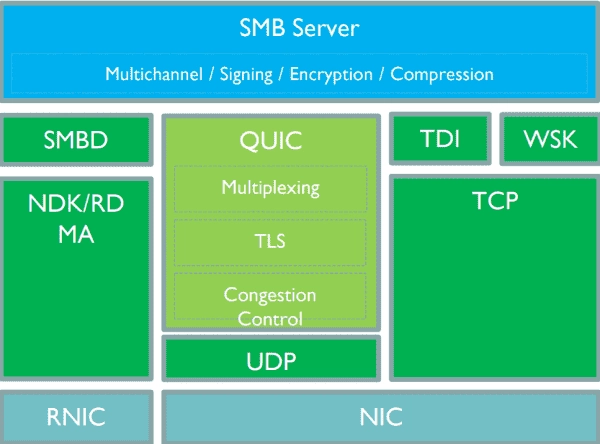
Transport options for Server Message Block SMB
Within the QUIC tunnel, SMB behaves as usual from the user’s point of view, and features such as multi-channel and compression are still available.
SMB over QUIC as the preferred protocol in the future
Due to these characteristics, Microsoft has positioned SMB over QUIC as a feature for edge servers, i.e., file servers running in the cloud or DMZ accessible over the internet. This was the reason for restricting QUIC support to the Azure Edition, which runs in the Microsoft Cloud or on-premises on Azure Stack HCI.
The announcement of SMB over QUIC for Windows Server 2025 aligns with the overall repositioning of the feature as a secure alternative to SMB over TCP. It hardens file servers even for internal use, and protects NTLM credentials against leakage. As a result, QUIC will become the preferred transport mechanism for SMB.
QUIC Client Access Control
Windows Server 2022 includes a new feature for limiting access to file servers via QUIC for specific clients. As it currently stands, a server allows all clients whose certificate chains to the same root certificate as the one used for QUIC on the server.
This new limitation also revolves around certificates. Administrators can add the fingerprints of client certificates to a trusted devices list on the server. This allows the server to determine, using the transmitted certificate data, whether a client is permitted access.
However, for larger settings, managing the thumbprints of all client certificates on the server could become laborious. That’s why QUIC Client Access Control also supports Secure Access Network (SAN) certificates, which can include the names of multiple hosts.
Enabling SMB over QUIC
The Windows Server Insider Preview Build 25997 includes SMB over QUIC for all editions, including Standard and Datacenter. By default, the feature is disabled and must be enabled by the server admin. Clients cannot enforce the use of the protocol.
The tools for activating SMB over QUIC remain the Windows Admin Center (WAC) and PowerShell. The current version of WAC is still limited to the Azure Edition for this task and denies QUIC configuration for other OS editions.
In PowerShell, the cmdlets responsible for this task are New-SmbServerCertificateMapping and Set-SmbServerConfiguration (see also: How to use SMB over QUIC in Windows Server 2022).
Summary
Microsoft initially positioned SMB over QUIC, introduced with Windows Server 2022, exclusively for accessing file servers via the internet. It was therefore only available in the Azure Edition. However, the enhanced security of the QUIC protocol also benefits purely on-prem environments.