Microsoft Network Monitor (NetMon) is a vital tool for capturing and analyzing network traffic on Windows systems. While it hasn’t seen updates in several years, many administrators still rely on it for diagnosing network connections. Although it may not match the complexity of tools like Wireshark, NetMon stands out for its simplicity and lightweight nature, making it suitable for various scenarios.
In an interesting case, a subscriber received a warning that their Windows VPS server was allegedly sending mass emails without authorization. To investigate further, they needed to identify the process responsible for initiating SMTP sessions, which added complexity as the mailings occurred sporadically. The task was to capture outgoing traffic on typical SMTP ports—25, 587, and 465—and determine the process that was sending these emails.
To begin, the user needed to download the Microsoft Network Monitor 3.4 installer (NM34_x64.exe) either from the Microsoft website or via the WinGet package manager:
winget install Microsoft.NetMonUpon installation, the user should run NetMon as an administrator and initiate a new capture. By default, all network traffic is collected, but to focus on the SMTP ports, specific filters must be applied.
The steps to set up the capture included going to Capture Settings and configuring the filters. Using a typical TCP port number filter, the user modified the template to capture traffic on all three SMTP ports:
tcp.port == 25 OR Payloadheader.LowerProtocol.port == 25 ORtcp.port == 587 OR Payloadheader.LowerProtocol.port == 587 ORtcp.port == 465 OR Payloadheader.LowerProtocol.port == 465To further refine the analysis, additional filters based on the computer’s source IP address may be added. Next, the parser profile should be set to "Windows" to ready the system for capturing traffic.
The user can then start capturing network data. It’s crucial to reproduce the original issue or allow the capture to run over an extended period to gather sufficient data.
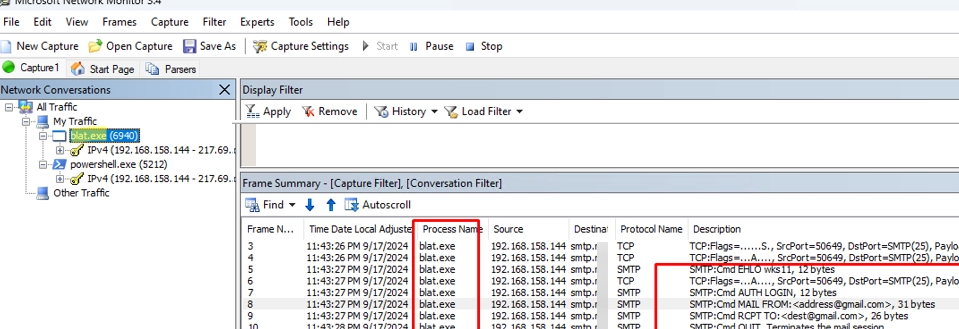
Eventually, relevant packets filtered by the settings will appear in the NetMon log. Each packet can be examined to view SMTP communication and related commands, helping to trace activities back to their source. The logs will display both the processes involved and the detailed SMTP commands, including authentication actions and destination servers.
In this instance, the analysis indicated that the sending mailings were emanating from a console tool known as blat.exe, while also highlighting the use of powershell.exe to check port availability on an external server.
Once the analysis is complete, capturing can be stopped, and the network traffic can be saved as a *.CAP file for offline evaluation. NetMon allows for additional filtering capabilities, including sorting by IP or MAC addresses, or delving deeper into specific protocols—ideal for those needing detailed analysis.
In conclusion, Microsoft Network Monitor remains a practical utility for those monitoring network traffic, and by following the outlined steps, users can effectively diagnose issues on their Windows systems. For further advanced monitoring and analysis, consider looking into built-in command-line tools like PktMon, which provide similar capabilities without the need for additional installations.