Prerequisites
To follow the steps in this post, you must have the following:
- Microsoft 365 tenant
- Either the Organization Management role in Exchange Online or the Security Administrator role in Microsoft 365
Every tenant in Microsoft 365 has three anti-spam policies by default. They are:
- Inbound
- Outbound
- Connection filter
These policies can be edited but not deleted. You can also create custom inbound or outbound policies. In the following section, we will understand the workings of each of these policies.
Inbound anti-spam policy
Emails sent to your users in Microsoft 365 are handled by the inbound anti-spam policy. This policy is present by default and cannot be disabled or deleted; however, you can edit it. All the users in your tenant are under the scope of this policy. If you wish to apply a different setting to specific users, you can create a new inbound anti-spam policy. In this section, we create a new inbound anti-spam policy.
You can access the Policies page through this
link.
Click Create policy and then select Inbound.
On the following page, give this policy a name and add a description, if needed. Then click Next.
Provide a name and a description that makes it easy to understand the purpose of the policy
You also need to decide the scope of this rule. This is shown on the next page, as shown in the screenshot below. These policies can be applied to individual users or distribution and security groups and domains. The recommended approach is to create a distribution group, add the required users to it, and select that group on this page. Here, we chose two users for the purpose of the demonstration.
Exceptions can be handled by checking the box for Exclude these users, groups and domains.
You can specify the users groups or domains to whom this rule would apply
On the next page, we will take a look at all the settings.
Anti spam settings configuration page
Here, we decide the level of control we want to exert on the users through this policy.
Bulk email threshold

Every email making contact with Exchange Online is given a bulk complaint level (BCL). This number represents the likelihood of an email being distributed in mass quantities. A BCL of zero signifies the email is not from a mass distributor, while figures like 8 or 9 suggest they emanate from mass distributors and multiple grievances have been lodged. Visit this link to understand BCL in further detail.
The standard BCL value in an anti-spam policy is set at 7. But this can be adjusted. It’s wise to maintain this figure at 7 to circumvent numerous false positives.
Spam properties
In this section, we provide the settings that lead to an increase in the value of the spam score, also known as the spam confidence level (SCL).
Configuring the spam properties
These settings are disabled by default. If you feel that your users are being targeted by these types of attacks, you can enable these conditions. Emails that match these conditions are marked with an SCL value of 5 or 6.
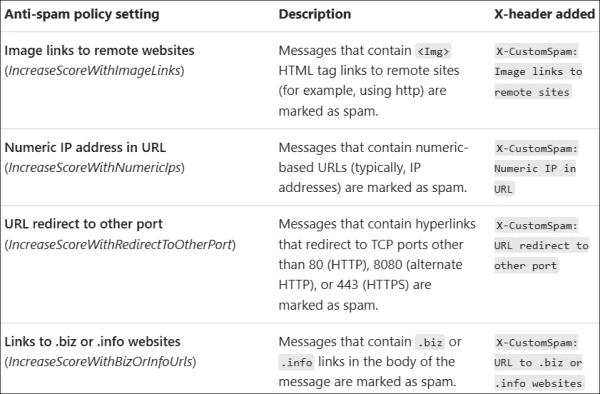
Meaning of each anti spam setting and its associated headers
Mark as spam
In this section, you can enable certain types of conditions to mark emails as spam. This will result in those emails being identified as high confidence spam with an SCL value of 9. The only exceptions are backscatter and sender ID filtering hard fail. All these are aggressive settings, and you should enable them only if you are certain that such emails need to be blocked.
Test mode
Emails matching any of the conditions set by you in this rule can be handled in different ways. One of these is test mode.
If you want to enable the rule immediately, choose None. However, if the intention is to test the rule, you can choose to add the default header value to the message headers of these emails. The value X-CustomSpam: This message was filtered by the custom spam filter option is added to the email’s header. Since this is testing mode, the policy won’t take any actions on the email, but only stamp the email’s header with this value.
The BCC Message option results in emails being sent to the recipient mentioned in the BCC field. This is again going to result in no action on the email and is only for testing the potential effect of your new rule.
Actions
You decide on the action that Microsoft 365 will take on emails matching the conditions you set in the previous sections. Emails can be marked as spam, high-confidence spam, phishing, high-confidence phishing, or as bulk senders. For each of these conclusions, we can select different actions, such as moving such emails to the user’s junk folder, moving them to the quarantine section, deleting or redirecting them, adding a header value, and even adding a statement to the subject of the email. These options are explained here.
The last section on this page has two more settings.
Safety tips
It is recommended that this be enabled, as users are then warned about emails being spam in Outlook. This reduces the chances of a user interacting with such emails.
Safety tips for Outlook clients
Safety tips for Outlook clients
Zero-hour auto purge (ZAP)
Zero-hour auto purge (ZAP) is a feature in Exchange Online that acts on emails that have already been delivered to the users’ mailboxes. If the emails are detected as spam or phishing, then they are handled, depending on the actions chosen for spam or phishing emails. ZAP can be enabled or disabled for either phishing or spam emails, or for both.
Click Next.
Allow and block list
On the next page, you have the option to add users or domains to the allowed list if you desire them to bypass your tenant’s security checks. Alternatively, you may add them to the blocked list if you wish to prevent those emails from being delivered.
You can add users or domains here to be either allowed or blocked
Click Next.
On the final page, review all the settings, and click Create if you are satisfied with them.
Outbound anti-spam policy

Emails sent from your tenant to the internet also require spam checking. If a mailbox from your tenant is misused to send malicious emails, your domain could get blacklisted or emails might get blocked by other organizations. This issue can be addressed by outbound anti-spam policies, which are invaluable in cases where spam or malicious emails are sent by internal users. This section will guide you through the settings required to create a new outbound anti-spam policy.
To reach the anti-spam policy page, follow this link. Click on the ‘Create policy’ button, then choose ‘Outbound’.
Once you navigate to the next page, assign a name and description to this policy.
On the following page, choose the users for whom this rule will take effect. This is explained in the previous section.
The next page is to configure the protection settings. The first section sets message limits.
Here we decide the limits of sending emails to external and internal recipients
External message limit
This governs the highest number of external recipients to whom users can send emails in an hour. For applications with the need to send bulk emails to external recipients, without changing the standard rule, a fresh anti-spam policy can be configured. It is crucial to input the maximum number of external recipients in this section for that particular application mailbox.
Internal message limit
The maximum number of internal recipients that users can email is determined by this field. This, too, serves to limit the potential harm a compromised mailbox could inflict.
Daily message limit
Mailboxes can also be restricted from emailing a specific number of users. This rule combines both internal and external recipients.
Restrictions placed on users who reach the message limit
You can choose the action you wish to take if a user exceeds the limits. Mailboxes can be stopped from sending emails for a day or even indefinitely. The third option is not to take any action; however, an alert can be generated. This was used to test the policy. If a user does breach the limits, the mailbox will be blocked. You can review this here.
Automatic forwarding rules: The automatic forwarding of emails to external recipients can pose risks. One can manage this through this rule.
- On—Automatic forwarding is permitted. However, enabling this isn’t advisable as it could result in mass emails being sent from your domain.
- Off—This rule disables the automatic forwarding of emails to external recipients. This is the preferred practice. It prevents compromised mailboxes from being utilised to send spam or harmful emails from your domain.
- Automatic system controlled—Automatic external forwarding is off. Microsoft adopts this setting to implement blocks on external email forwarding across all domains in Microsoft 365.
Notifications
Send a copy of suspicious outbound email that exceed these limits to these users and groups—One can select specific users or groups to be included in the BCC field of suspicious outbound emails. Note that this only applies to the default anti-spam policy and not to custom policies like this one.
Notify these users and groups if a sender is blocked due to sending outbound spam—Notifies email admins about user accounts restricted from sending emails. This enables administrators to respond promptly to potential account breaches. The alert policy User restricted from sending email informs the global admins about a user account being blocked. It is proposed that alert policies be used.
The last page is to review all the settings and then click Create.