-

Google Urges Regulators to Address Microsoft’s Cloud Practices, Claims Year-Long Inaction
Google Cloud has reiterated its concerns regarding Microsoft’s cloud licensing practices, claiming that a year after it lodged a complaint with the European Commission, no action has been taken to address the issue. The company argues that Microsoft’s licensing rules create a significant financial burden for customers wishing to migrate to rival cloud services like…
-
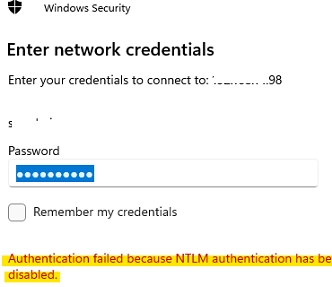
How to Block NTLM Connections on Windows 11 and Windows Server 2025
Microsoft has taken a significant step towards enhancing security by phasing out the deprecated NTLMv1 authentication protocol in Windows 11 version 24H2 and Windows Server 2025. The removal of support for NTLMv1 aims to encourage users to adopt more secure alternatives such as Kerberos. Additionally, Microsoft has indicated that NTLMv2 may also face deprecation in…
-

Exploring Windows Server: Features, Benefits, and Best Practices for Businesses
Following an internal team investigation, the Google Ads team recently dismissed multiple employees. These terminations came after an inquiry revealed misconduct related to the advertisement approval process. Some of the individuals reportedly violated company policies by approving ads that did not meet the required advertising guidelines. The terminations reflect Google’s ongoing efforts to uphold integrity…
-

Troubleshooting: Windows Stuck at ‘Getting Windows Ready, Don’t Turn Off Your Computer’ Screen
This issue of Windows getting stuck at the "Getting Windows Ready. Don’t turn off your computer" message is fairly common, especially on Windows Server versions (2022, 2019, 2016) and occasionally on Windows 10 and 11. This often occurs after installing updates or modifying system roles and features. When encountering this message, the best initial advice…
-

September Patch Tuesday: Essential Updates for Windows, Office, and SQL Server
Microsoft released 86 patches this month, addressing key issues in Windows, Office, and SQL Server, and importantly, there were no zero-day vulnerabilities identified. This release indicates a sign of progress from Microsoft’s update team, as updates to the browser platform were rated as “moderate” security risks instead of more urgent classifications. For those looking for…
-

A Step-by-Step Guide to Installing IIS on Windows Server
If you want to host websites or web applications on a Windows Server, the first step is to install Internet Information Services (IIS). While IIS is included with Windows Server, it is not enabled by default, so you’ll need to take some steps to get it running. How to Install IIS via Server Manager Open…
-

How to Delete a Service in Windows Server: A Step-by-Step Guide Using Command Prompt and Registry Editor
Ever had a service in Windows Server that you wanted to delete but it keeps running in the background? This can happen with an old application that left its service behind or a test service that is no longer relevant. Removing such unused services can help clean up your server, reduce resource consumption, and prevent…
-

Beware the Ghastly GhostRedirector Gang: How They’re Hijacking Windows Servers for SEO Manipulation
Security researchers at ESET have identified a new hacking group known as GhostRedirector, which is employing advanced tactics to target Windows servers. This group aims to manipulate search engine rankings through a service dubbed SEO fraud. GhostRedirector uses custom tools, specifically a malware called Rungan, which installs a backdoor on compromised machines, providing the hackers…
-

Windows Update Causes App Installation Failures: Here’s the Fix You Need
If you’ve encountered an increase in User Account Control (UAC) prompts or faced issues with application installations and repairs on Windows, the root cause may stem from a recent security update intended for Windows and Windows Server. Fortunately, Microsoft has shared a straightforward workaround designed for home users. However, those utilizing work computers without administrative…
-

KB5063878: Microsoft Acknowledges UAC Changes Impacting App Installations on Windows 10 & 11
Microsoft recently issued an August 2025 security update, KB5063878, which introduces significant changes affecting User Account Control (UAC) during Windows Installer (MSI) repair operations. The update mandates the need for administrator credentials, addressing a security vulnerability recognized as CVE-2025-50173. As a result of this enforcement, standard users may face UAC prompts in various situations, such…