A user account lockout in a domain is one of the most popular reasons why users contact the technical support team. In most cases, the lockout is caused either by a user forgetting their password or by an application trying to use a previous (saved) password for authentication after the user has changed it.
Account Lockout Policy in Active Directory
User account lockout is enabled in the default security policies of an Active Directory domain.
Normally, the settings for user lockout are set up in the Default Domain Policy GPO (Configuration -> Windows Settings -> Security Settings -> Account Policy -> Account Lockout Policy). There are three settings available:
- Account lockout threshold – the number of unsuccessful attempts allowed for password entry, after which the user’s account gets locked;
- Account lockout duration – the amount of time in minutes that the user’s account stays locked. Once this duration expired, the user’s account will be unlocked automatically;
- Reset account lockout counter after – the number of minutes after which the failed log-in attempts counter is reset.
All these lockout settings are applicable on all domain users, apart from groups that have certain special settings applied using Fine-Grained Password Policies.
Gain more knowledge about password policies in AD.
The Microsoft security baselines recommend that users should be locked out after 10 failed login attempts. This is considered optimal for protecting against password brute-force and DoS attacks, and is convenient for users who often make mistakes when entering their passwords.
The default password policy in Entra ID (ex. Azure AD) locks a user account after 10 failed attempts to log in.
How to Unlock a User Account Using the Active Directory Console (ADUC)
If a user account is locked out, you will see the message below when trying to log on to Windows:
The referenced account is currently locked out and may not be logged on to.
If a domain user frequently complains that their account is locked out, you can find a computer and process that are constantly causing lockouts by looking for event IDs 4740 and 4625 in the Primary Domain Controller security log (see How to find account lockout source in Active Directory).
A user will not be able to log on to Windows until the lockout period expires or an administrator manually unlocks the account.
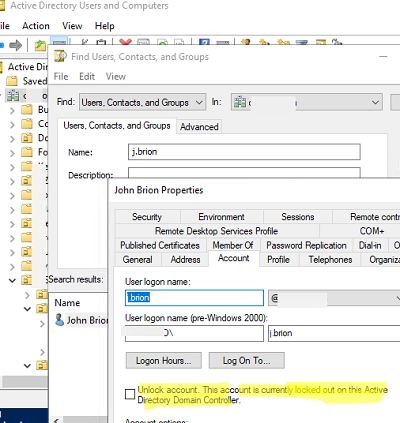
You can unlock a user using the Active Directory Users and Computers (ADUC) graphical console:
- Open the
dsa.mscconsole and find the AD user you want to unlock; - Click the Account tab. If the user is locked, there should be a message here
Unlock account. This account is currently locked out on this Active Directory Domain Controller; - Check this option and click OK to save the changes;
- The user account is unlocked and may be used to log on domain.
By default, only domain admins can unlock users in AD. You can delegate unlock permissions to non-admin users so that they can unlock accounts.
- Click the Organization Unit (OU) containing the users you want to delegate permissions to and select Delegate Control;
- Select a group of users you want to grant permissions to (for example, nyHelpDesk);
- Then select Create a custom task -> Only the following objects in the folder -> User objects;
- In the list of permissions, tick the Write lockoutTime box;
- Now members of the nyHelpDesk group can unlock users.
You can enable an audit policy that allows you to find out who unlocked a user account:
- Enable the Audit User Account Management policy in
Default Domain ControllerGPO (Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Advanced Audit Policy Configuration -> Audit Policies -> Account Management); - You can then track user unlock events by looking for EventID 4767 in the Security log on the domain controller (
A user account was unlocked); - You can also use PowerShell to find events by event ID:
Get-WinEvent -FilterHashtable @{logname='Security';id=4767}|ft TimeCreated,Id,Message
Increase Event Viewer log size on domain controllers to store more events.
Unlock AD Accounts Using PowerShell
You can use the Unlock-ADAccount PowerShell cmdlet to unlock AD users. This cmdlet is included in the AD Module for Windows PowerShell.
Check that the user is locked (Lockedout = true):
Get-ADUser -Identity j.brion -Properties LockedOut,DisplayName | Select-Object samaccountName, displayName,Lockedout
Unlock the AD user with the command:
Unlock-ADAccount j.brion
You can use PowerShell to view the lockout time, the last logon date, and the date that the user’s password was changed:
<code>Get-ADUser j.brion -Properties Name,Lockedout, lastLogonTimestamp,lockoutTime,pwdLastSet | Select-Object Name, Lockedout,@{n=’LastLogon’;e={[DateTime]::FromFileTime($_.lastLogonTimestamp)}},@{n=’lockoutTime’;e={[DateTime]::FromFileTime($_.lockoutTime)}},@{n=’pwdLastSet’;e={[DateTime]::FromFileTime($_.pwdLastSet)}}</code>
You can use the <a href=”https://woshub.com/how-to-find-blocked-disabled-or-inactive-objects-in-ad-using-search-adaccount/” rel=”nofollow” target=”_blank”>Search-ADAccount cmdlet</a> to find all the locked users in the domain:
<code>Search-ADAccount -UsersOnly -lockedout</code>
With a simple PowerShell one-liner, you can unlock all domain users at once:
Search-ADAccount -UsersOnly -lockedout| Unlock-ADAccount