Microsoft has taken a significant step towards enhancing security by phasing out the deprecated NTLMv1 authentication protocol in Windows 11 version 24H2 and Windows Server 2025. The removal of support for NTLMv1 aims to encourage users to adopt more secure alternatives such as Kerberos. Additionally, Microsoft has indicated that NTLMv2 may also face deprecation in future updates.
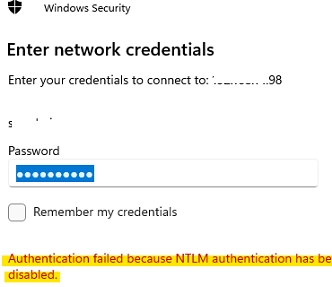
When attempting to connect to devices that only support NTLMv1, users will face an authentication error, stating:
Authentication failed because NTLM authentication has been disabled.In the Event Viewer, these connection attempts will trigger an event log displaying:
ERROR_NTLM_BLOCKEDError code: 1937 (0x791)Users trying to connect via Remote Desktop Protocol (RDP) to a Windows 11 24H2 domain device from a workgroup computer may see an error like:
An authentication error has occurred.The function requested is not supported.This could be due NTLM authentication being blocked on the remote computer.This lack of NTLMv1 support is likely to affect connectivity, especially with devices like Synology NAS and TrueNAS that rely on this outdated protocol. To maintain compatibility, users may need to update their devices to support at least NTLMv2.
Auditing NTLMv1 Usage
Windows 11 24H2 and Windows Server 2025 also come with improved auditing for NTLM authentication. Now, users can track NTLM authentication attempts (both v1 and v2) through the Event Viewer under:
Applications and Services Logs -> Microsoft -> Windows -> NTLM -> Operational
These logs will detail:
- The user and process attempting NTLM authentication
- The version of NTLM used
- The name or IP address of the requesting device
By default, NTLM usage auditing is turned on, but it can be disabled through Group Policy settings. On Active Directory domain controllers, this is controlled via the Log Enhanced Domain-wide NTLM Logs option.
Even with the depreciation of NTLMv1, it may still be used occasionally through legacy algorithms, like MS-CHAPv2 in certain AD domains. To safeguard against the use of legacy protocols, Microsoft recommends enabling Credential Guard on devices.
A roadmap for NTLMv1 deprecation highlights several key dates:
- NTLMv1 usage auditing was activated in August 2025.
- Full enforcement of these settings is expected in October 2026, where NTLMv1 will be blocked by default unless manually changed.
Blocking NTLM Over SMB
In addition, Windows 11 and Windows Server 2025 allow users to disable NTLM authentication for SMB connections. Admins can utilize PowerShell commands to enforce this:
To completely disable NTLM for SMB clients:
Set-SMbClientConfiguration -BlockNTLM $trueOr disable it for specific mapped drives:
New-SmbMapping -RemotePath \srv1shared -BlockNTLM $trueFurthermore, there’s an option to limit the time between failed NTLM authentication attempts, providing additional security against brute force attacks on SMB shared folders.
These advancements represent Microsoft’s ongoing commitment to improving security protocols and reducing reliance on outdated and insecure authentication methods. It is essential for organizations to prepare for these changes and ensure their environments continue to function smoothly after the transition away from NTLMv1.