Cybersecurity researchers have reported a severe design flaw in the Delegated Managed Service Accounts (dMSAs) introduced with Windows Server 2025. This vulnerability could lead to high-impact attacks, allowing adversaries to move laterally across domains and achieve persistent access to all managed service accounts within Active Directory.
This flaw enables attackers to bypass authentication measures and create passwords for both dMSAs and Group Managed Service Accounts (gMSAs). Dubbed the Golden dMSA attack, the method has been characterized as low complexity, primarily because the vulnerability facilitates brute-force password generation.
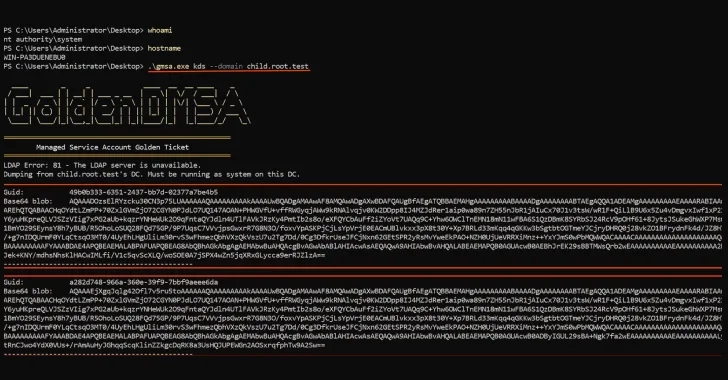
For successful exploitation, attackers must access a Key Distribution Service (KDS) root key, typically available only to privileged accounts, including Domain Admins and Enterprise Admins. This KDS root key is pivotal as it serves as the master key, letting an attacker derive current passwords of any dMSA or gMSA without direct access to the domain controller.
The design flaw involves predictable time-based components in the password generation structure, limiting potential combinations to just 1,024. Security researcher Adi Malyanker explained that this makes brute-force attacks trivial.
The dMSA feature was designed to facilitate the transition from legacy service accounts and guard against Kerberoasting attacks. However, if compromised, a single KDS root key allows attackers to penetrate and control dMSAs across all domains within a corporate forest.
The typical attack modus operandi includes extracting KDS root key material by escalating privileges on a domain controller, enumerating dMSA accounts, guessing passwords, and generating valid credentials for compromised accounts, all without needing further elevated access once the KDS root key is secured.
As a result, this flaw transforms individual breaches into enterprise-wide vulnerabilities, allowing attackers to harvest credentials and move laterally across the network with ease. Even in environments utilizing multiple KDS keys, the oldest key can be exploited effectively, creating a long-term backdoor.
Microsoft acknowledged the issue following its responsible disclosure, noting that if the secrets used to produce the key are exposed, attackers can authenticate as the user. This alarming susceptibility highlights the critical security oversight in managed service accounts, as they depend on these domain-level cryptographic keys for security.
To mitigate these risks, it is essential for organizations to understand the implications of the Golden dMSA attack and enhance their security measures against potential exploits. Microsoft has also released a proof-of-concept to demonstrate the vulnerability, emphasizing the need for immediate action to secure systems against such design flaws.